this post was submitted on 23 Oct 2024
1175 points (98.4% liked)
Malicious Compliance
19347 readers
1552 users here now
People conforming to the letter, but not the spirit, of a request. For now, this includes text posts, images, videos and links. Please ensure that the “malicious compliance” aspect is apparent - if you’re making a text post, be sure to explain this part; if it’s an image/video/link, use the “Body” field to elaborate.
======
-
We ENCOURAGE posts about events that happened to you, or someone you know.
-
We ACCEPT (for now) reposts of good malicious compliance stories (from other platforms) which did not happen to you or someone you knew. Please use a [REPOST] tag in such situations.
-
We DO NOT ALLOW fiction, or posts that break site-wide rules.
======
Also check out the following communities:
[email protected] [email protected]
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
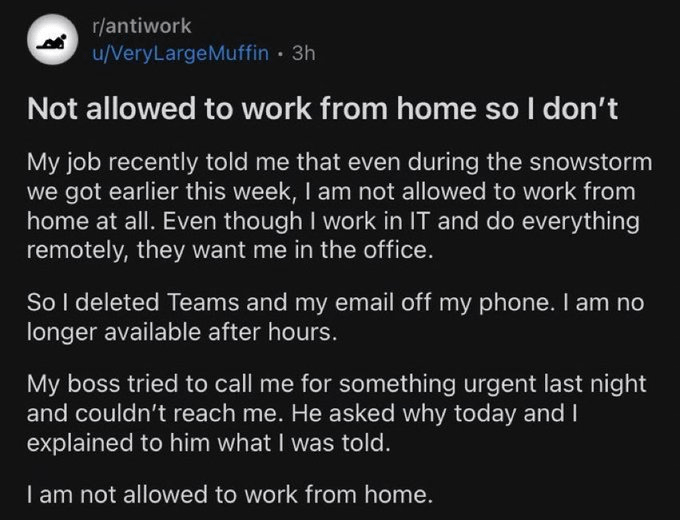
Eh, it doesn't need to be, you just need to do the work of putting together granular access controls that can account for your risk profiles.
The risk isn't much different between a company owned telephone and a personal telephone.
They're both susceptible to most of the same attacks, or being left on the bus.