I'm personally motivated in a non-commercial way to supply everyone with as much cybersecurity as possible in the interests of civlization, especially now. I've just finished what I wanted to releae as "set" 2 days ago and it's time to announce them.
I'm the former Web Application Security Team Lead for the National Computer Center, Research Triangle Park, having been contracted to the EPA by the now defunct Computer Sciences Corporation.
If you have some extra hardware not really being used I would suggest perhaps a great use of it would be to create yourself a hardened platform, just in case, to protect your sensitive data on an emminently stable platform going forward.
Maybe you've always wanted to try a BSD, well now is a great time to do that. They are super stable, super reliable, community drive, and you are in control of everything.
I would also like to mention that if you'd like to go extra hard consider Hardened BSD. Another alternative is using grsecurity/PaX kernel patched Alpine Linux as a Desktop choosing crypt full disk encryption during setup + AppArmor.
Just as an example you can get your hands on a $250 Thinkpad T495 and installing GhostBSD on it is as simple to setup as Linux Mint and runs as fast as a brand new 2023 Windows laptop. If you choose Dragonfly BSD, the fastest BSD, on a T495 (the lastest year fully BSD compatible laptop), my repo will completely configure it for you, complete with all applications needed for a professional developer.
In addition to that I've created a Network Based Firefox hardening solution that wipes the extremely profitable, For-Profit, Mozilla Corporation off your Internet and easily combines with Arkenfox. It removes Mozilla servers from being contacted by any application or service on your machine and does not interfere with web page rendering.
I've created my own Git Repository using Gogs (which Gitea is based on) where you can get all the goods here:
Latest Software
https://quadhelion.dev
Main Website
https://www.quadhelion.engineering
About
https://www.quadhelion.engineering/about.html
Backup GitHub
https://github.com/wravoc
Backup BitBucket
https://bitbucket.org/quadhelion-engineering/workspace/repositories/
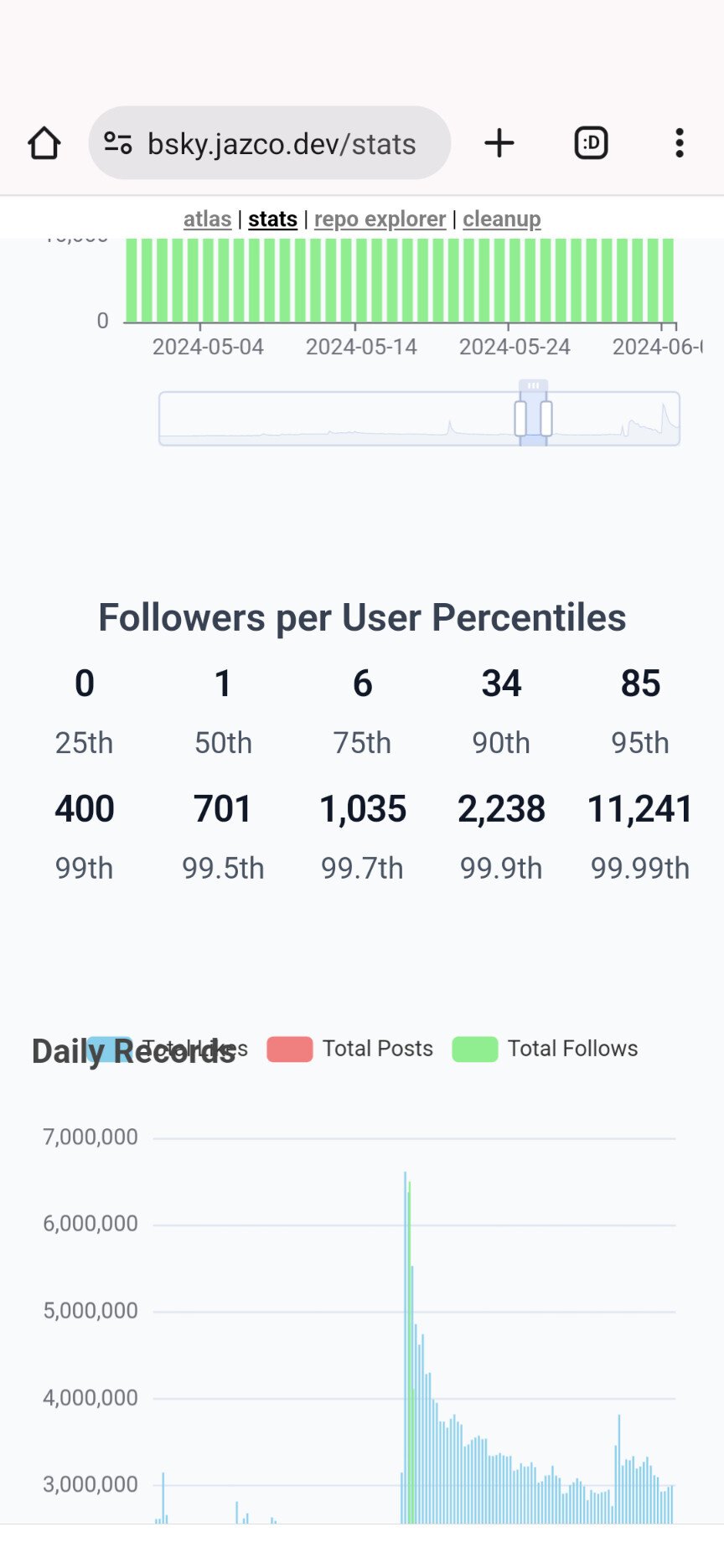






Plus, check this out. The platform says I have 12 followers but only 4 show up. Major problems over there.