Thousands of Android APKs use compression trick to thwart analysis

Threat actors increasingly distribute malicious Android APKs (packaged app installers) that resist decompilation using unsupported, unknown, or heavily tweaked compression algorithms.
The main advantage of this approach is to evade detection by security tools using static analysis and hamper examination by researchers, delaying the development of an in-depth understanding of how an Android malware strain works.
Zimperium, a member of the 'App Defense Alliance' dedicated to identifying and eliminating malware from Google Play, analyzed the decompilation resistance landscape after a Joe Security tweet that showcased an APK that eludes analysis yet runs seamlessly on Android devices.
A zLab report published yesterday claims 3,300 APKs are using these unusual anti-analysis methods, which might cause many of them to crash. However, the researchers found a subset of 71 malicious APKs that work fine on Android OS version 9 (API 28) and later.
Zimperium clarifies that none of these apps are on the Google Play store but lists their hashes at the bottom of the report to help people who source apps from third-party stores find and uninstall them.
Compression tricks
Android APKs use the ZIP format in two modes, one without compression and one using the DEFLATE algorithm.
APKs packed using unsupported or unknown compression methods are not installable on Android 8 and older, but they will work fine on Android versions 9 and later.
Zimperium tested the apps it sampled on decompressor tools like JADX, APKtool, and the macOS Archive Utility, and none of them could unzip the APK for analysis.
In addition to using unsupported compression methods, Zimperium also found that malicious APK authors use filenames that surpass 256 bytes to cause crashes on analysis tools, corrupt the AndroidManifest.xml file for obfuscation, and use malformed String Pools to crash tools that parts Android XML files.
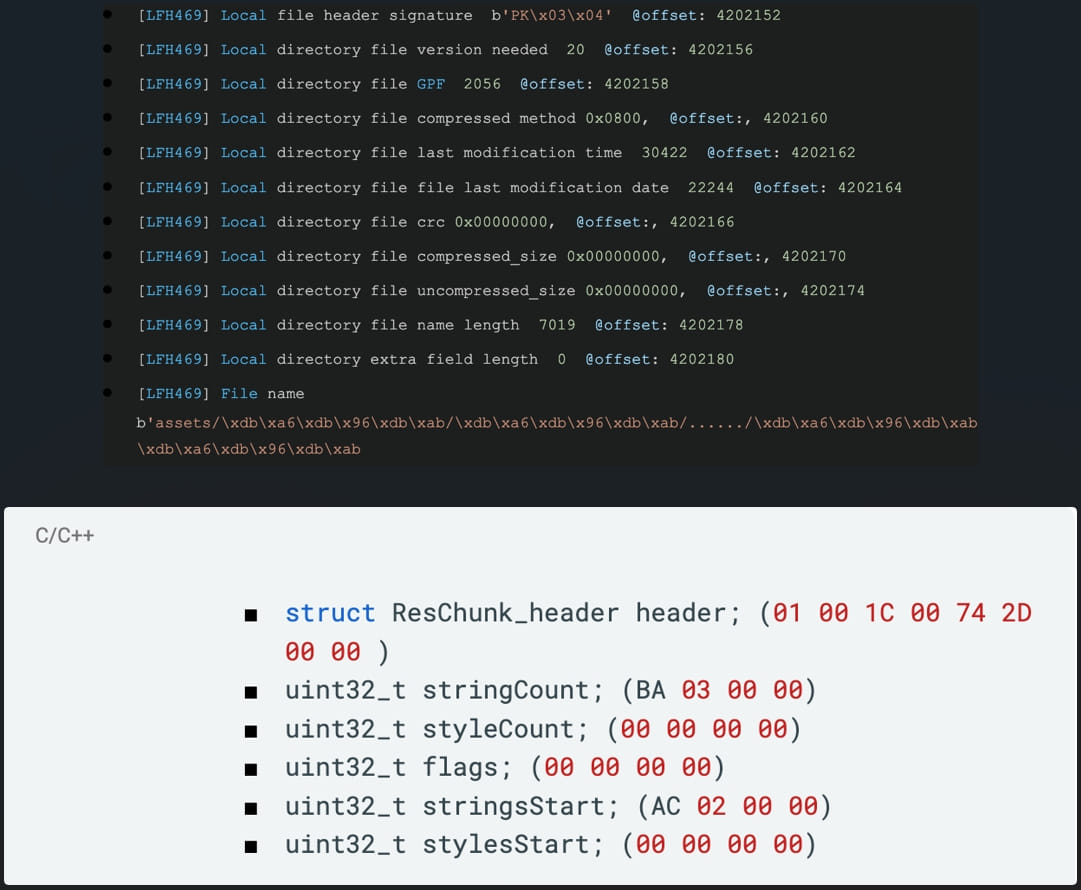
Exceedingly long filename (top), malformed string pool header (bottom) (Zimperium)
These are all anti-analysis techniques, and while Zimperium doesn't delve into what those malicious APKs do exactly, the intent to conceal their functions is unlikely to be benign.
Since APKs downloaded from outside Google Play cannot be vetted, the best way to protect against these threats is to avoid installing Android apps from third-party sites in the first place.
If you must install an app outside of Google Play, scan it with a reputable mobile AV tool before installation.
During app installation, pay attention to the requested permissions and look for any red flags unrelated to the app's core functionality.
Finally, "rooting" your Android device makes the user an administrator, allowing malicious APKs to run at the highest privileges on the OS, so this is generally discouraged.