LinkedIn accounts hacked in widespread hijacking campaign

LinkedIn is being targeted in a wave of account hacks resulting in many accounts being locked out for security reasons or ultimately hijacked by attackers.
As reported today by Cyberint, many LinkedIn users have been complaining about the account takeovers or lockouts and an inability to resolve the problems through LinkedIn support.
"Some have even been pressured into paying a ransom to regain control or faced with the permanent deletion of their accounts," reports Cyberint's researcher Coral Tayar.
"While LinkedIn has not yet issued an official announcement, it appears that their support response time has lengthened, with reports of a high volume of support requests."
A small sample of the numerous user reports on X
(BleepingComputer)
From complaints seen by BleepingComputer on Reddit, Twitter, and the Microsoft forums, LinkedIn support has not been helpful in recovering the breached accounts, with users just getting frustrated by the lack of response.
"My account was hacked 6 days ago. Email was changed in the middle of the night and I had no ability to confirm the change or prevent it," wrote an affected user in Reddit thread about the hacks.
"No response from them anywhere. It's pathetic. I tried reporting my hacked account, going through identity verification, and even DMing them on @linkedinhelp on twitter. No responses anywhere. What a joke of a company.."
Cyberint says there are also signs of a breakout reflected in Google Trends, where search terms about LinkedIn account hack or recovery record an increase of 5,000% over the past few months.
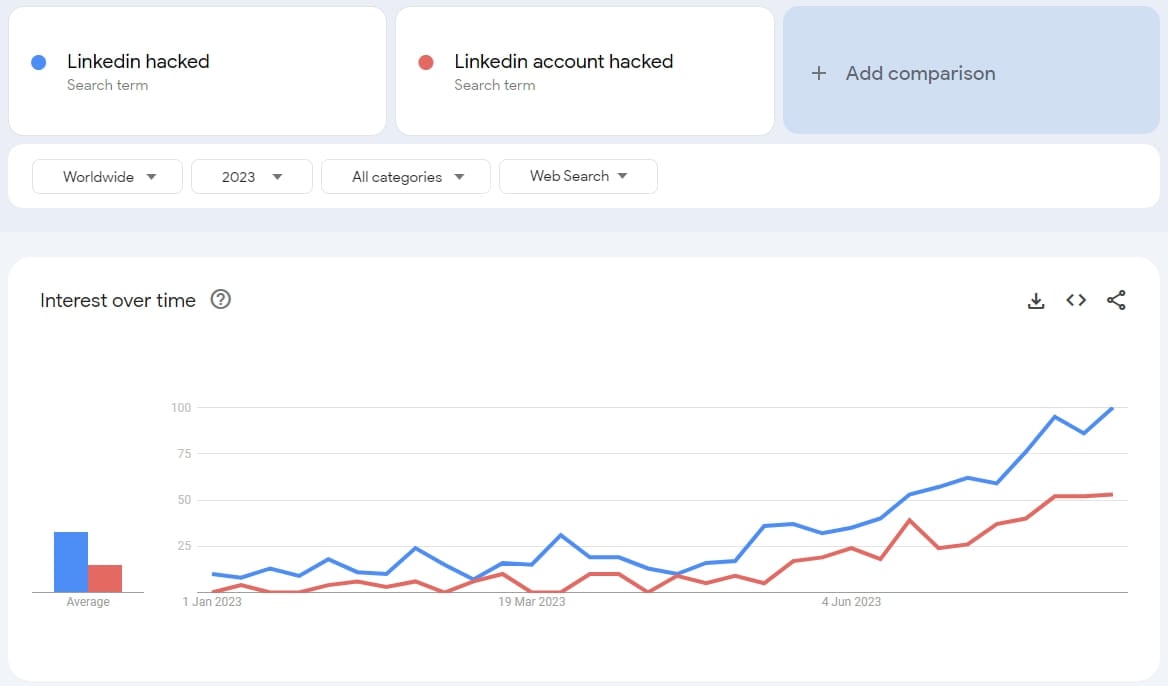
Google Trends indicate atypical activity (BleepingComputer)
The attackers appear to be using leaked credentials or brute-forcing to attempt to take control of a large number of LinkedIn accounts.
For accounts that are appropriately protected by strong passwords and/or two-factor authentication, the multiple takeover attempts resulted in a temporary account lock imposed by the platform as a protection measure.
Owners of these accounts are then prompted to verify ownership by providing additional information and also update their passwords before they're allowed to sign in again.
When the hackers successfully take over poorly protected LinkedIn accounts, they quickly swap the associated email address with one from the "rambler.ru" service.
After that, the hijackers change the account password, preventing the original holders from accessing their accounts. Many of the users also reported that the hackers turned on 2FA after hijacking the account, making the account recovery process even more difficult.
In some cases observed by Cyberint, the attackers demanded a small ransom to give the accounts back to the original owners or outright deleted the accounts without asking for anything.
LinkedIn accounts can be valuable for social engineering, phishing, and job offer scams that sometimes lead to multi-million dollar cyber-heists.
Especially after LinkedIn introduced features that combat fake profiles and inauthentic behavior on the platform, hijacking existing accounts has become much more pragmatic for hackers.
If you maintain a LinkedIn account, now would be a good time to review the security measures you've activated, enable 2FA, and switch to a unique and long password.
BleepingComputer has contacted LinkedIn requesting a comment on the reported situation, but we have not received a response by publication time.