Lapsus$ hackers took SIM-swapping attacks to the next level

The U.S. government released a report after analyzing simple techniques, e.g. SIM swapping, used by the Lapsus$ extortion group to breach dozens of organizations with a strong security posture.
Reviewing the group’s operations started in December last year following a long trail of incidents attributed to or claimed by Lapsus$ after leaking proprietary data from alleged victims.
Among high-profile companies impacted by Lapsus$ are Microsoft, Cisco, Okta, Nvidia, T-Mobile, Samsung, Uber, Vodafone, Ubisoft, and Globant.
Lapsus$ is described as a loosely-organized group formed mainly of teenagers, with members in the U.K. and Brazil that acted between 2021 and 2022 for notoriety, financial gain, or for fun. However, they also combined techniques of various complexity with “flashes of creativity.”
SIM-swap power
The Department of Homeland Security (DHS) Cyber Safety Review Board (CSRB) finalized its analysis and describes the group’s tactics and techniques in a report that also includes recommendations for the industry.
“Lapsus$ employed low-cost techniques, well-known and available to other threat actors, revealing weak points in our cyber infrastructure that could be vulnerable to future attacks” - Department of Homeland Security Cyber Safety Review Board.
The group used SIM swapping to gain access to a target company’s internal network and steal confidential information like source code, details about proprietary technology, or business and customer-related documents.
In a SIM-swapping attack, the threat actor steals the victim’s phone number by porting it to a SIM card owned by the attacker. The trick relies on social engineering or an insider at the victim’s mobile carrier.
With control over the victim’s phone number, the attacker can receive SMS-based ephemeral codes for two-factor authentication (2FA) required to log into various enterprise services or breach corporate networks.
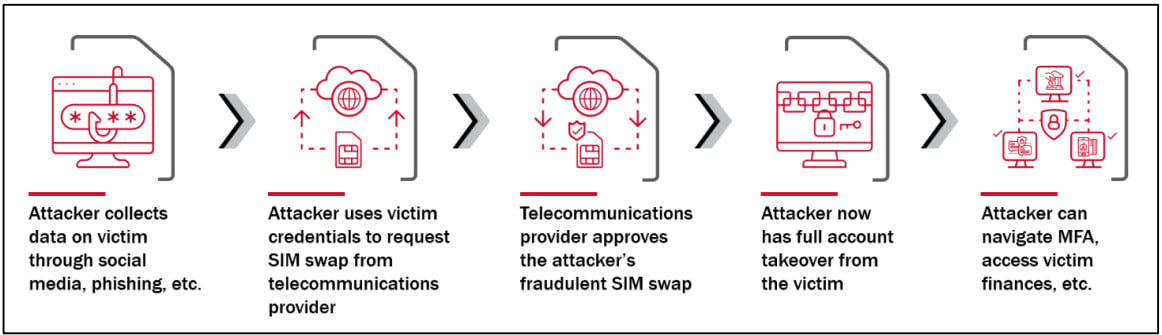
Fraudulent SIM-swap chain of events
source: DHS CSRB
Going to the source
In the case of Lapsus$, some of the fraudulent SIM swaps were performed straight from the telecommunications provider’s customer management tools after hijacking accounts belonging to employees and contractors.
To obtain confidential information about their victim (name, phone number, customer proprietary network information), members of the group sometimes used fraudulent emergency disclosure requests (EDRs).
An attacker can create a fake EDR by impersonating a legitimate requestor, such as a law enforcement agent, or by applying official logos to the request.
Lapsus$ also relied on insiders at targeted companies, employees, or contractors, to obtain credentials, approve multi-factor authentication (MFA) requests, or use internal access to help the threat actor.
“After executing the fraudulent SIM swaps, Lapsus$ took over online accounts via sign-in and account recovery workflows that sent one-time links or MFA passcodes via SMS or voice calls” - Department of Homeland Security Cyber Safety Review Board.
In one case, Lapsus$ used their unauthorized access to a telco provider to try to compromise mobile phone accounts connected to FBI and Department of Defense personnel.
The attempt was unsuccessful due to extra security implemented for those accounts.
Making and spending money
During the research, CSRB’s findings, the group paid as much as $20,000 per week to access a telecommunications provider’s platform and perform SIM swaps.
Although the FBI was not aware of Lapsus$ selling the data they stole or found evidence of victims paying ransoms to the group, CSRB says that some security experts “observed Lapsus$ extorting organizations with some paying ransoms.”
According to CSRB’s findings the group also exploited unpatched vulnerabilities in Microsoft Active Directory to increase their privileges on the victim network.
It is estimated that Lapsus$ leveraged Active Directory security issues in up to 60% of their attacks, showing that members of the group had the technical skills to move inside a network.
Hitting the brakes
While Lapsus$ was characterized by effectiveness, speed, creativity, and boldness, the group was not always successful in its attacks. It failed in environments that implemented application or token-based multi-factor authentication (MFA).
Also, robust network intrusion detection systems and flagging suspicious account activity prevented Lapsus$ attacks. Where incident response procedures were followed, the impact was “significantly mitigated,” CSRB says in the report.
Despite security researchers and experts decrying for years the use of SMS-based authentication as insecure, DHS’ Cyber Safety Review Board highlights that “most organizations were not prepared to prevent” the attacks from Lapsus$ or other groups employing similar tactics.
The Board’s recommendations to prevent other actors from gaining unauthorized access to an internal network include:
- transitioning to a passwordless environment with secure identity and access management solutions and discarding SMS as a two-step authentication method
- prioritizing efforts to reduce the efficiency of social engineering through robust authentication capabilities that are resilient to MFA phishing
- telco providers should treat SIM swaps as highly privileged actions that require strong identity verification, and provide account-locking options for consumers
- strengthen Federal Communications Commission (FCC) and Federal Trade Commission (FTC) oversight and enforcement activities
- planning for disruptive cyberattacks and investing in prevention, response, and recovery; adopting a zero-trust model and strengthening authentication practices
- building resilience against social engineering attacks when it comes Emergency Disclosure (Data) Requests
- organizations should increase cooperation with law enforcement by reporting incidents promptly; the U.S. Government “clear, consistent guidance about its cyber incident-related roles and responsibilities”
Lapsus$ fell silent since September 2022, likely due to law enforcement investigations that led to the arrests of several members of the group.
In March last year, the City of London Police announced the arrest of seven individuals linked to Lapsus$. A few days later, on April 1, two more were apprehended, a 16-year-old and a 17-year-old.
In October, during Operation Dark Cloud, the Brazilian Federal Police arrested an individual suspected to be part of the Lapsus$ extortion group, for breaching the systems of the country’s Ministry of Health.