Gafgyt malware exploits five-years-old flaw in EoL Zyxel router

Fortinet has issued an alert warning that the Gafgyt botnet malware is actively trying to exploit a vulnerability in the end-of-life Zyxel P660HN-T1A router in thousands of daily attacks.
The malware targets CVE-2017-18368, a critical severity (CVSS v3: 9.8) unauthenticated command injection vulnerability in the device's Remote System Log forwarding function, which was patched by Zyxel in 2017.
Zyxel previously highlighted the threat from the then-new Gafgyt variant in 2019, urging users still using an outdated firmware version to upgrade to the latest release to protect their devices from takeover.
However, Fortinet continues to see an average of 7,100 attacks per day since the beginning of July 2023, with the volume of attacks continuing today.
"[As of] Aug 7, 2023, FortiGuard Labs continue to see attack attempts targeting the 2017 vulnerability and has blocked attack attempts of over thousands of unique IPS devices over the last month," reads a new Fortinet outbreak alert released today.
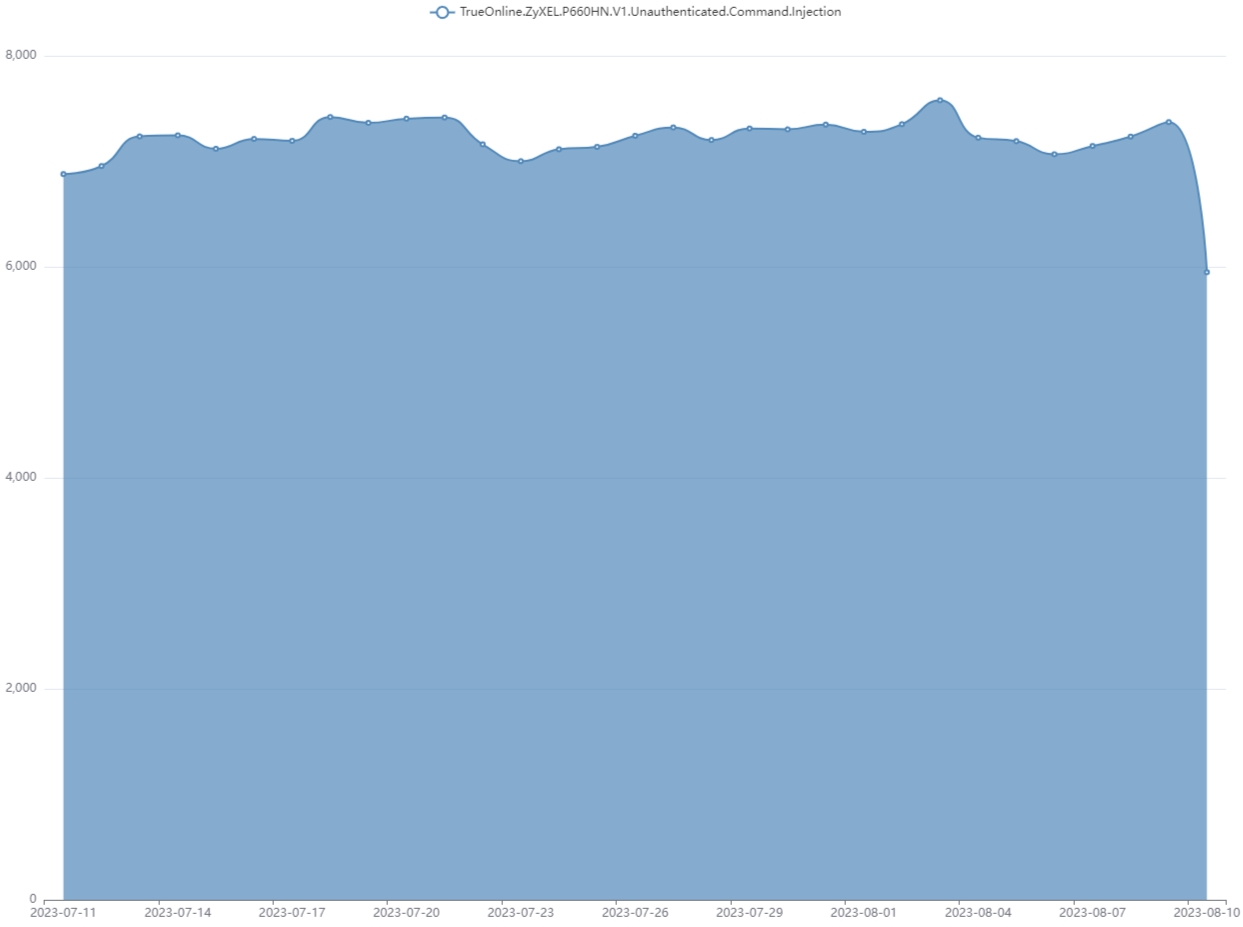
Attempts to exploit CVE-2017-18368 in Zyxel routers
Source: Fortinet
It is unclear what portion of the observed attack attempts resulted in successful infections. However, the activity has remained at a steady volume since July.
CISA also warned this week about the active exploitation of CVE-2017-18368 in the wild, adding the flaw to its catalog of known exploited vulnerabilities.
The cybersecurity agency now requires federal agencies to patch the Zyxel vulnerability by August 28th, 2023.
In response to the exploitation outbreak, Zyxel updated its security advisory, reminding customers that CVE-2017-18363 only impacts devices running firmware versions 7.3.15.0 v001/3.40(ULM.0)b31 or older.
P660HN-T1A routers running the latest firmware version made available in 2017 to remediate the flaw, version 3.40(BYF.11), are not impacted by these attacks.
However, the vendor highlights that the device has reached end-of-life and is no longer supported, so switching to a newer model would be wise.
"Please note that the P660HN-T1A reached end-of-life several years ago; therefore, we strongly recommend that users replace it with a newer-generation product for optimal protection," warns Zyxel.
Common signs of botnet infections on routers include unstable connectivity, device overheating, sudden configuration changes, unresponsiveness, atypical network traffic, opening up of new ports, and unexpected reboots.
If you suspect a compromise from botnet malware, perform a factory reset, update your device firmware to the latest version, and change the default admin user credentials.
Also, it advised that you disable the remote administration panel and only manage the devices from your internal network.