MoustachedBouncer hackers use AiTM attacks to spy on diplomats

Image: Midjourney
A cyberespionage group named 'MoustachedBouncer' has been observed using adversary-in-the-middle (AitM) attacks at ISPs to hack foreign embassies in Belarus.
According to an ESET report released today, the researchers observed five distinct campaigns, with the threat actors believed to be active since at least 2014, using AitM at Belarusian ISPs since 2020.
The two signature malware frameworks MoustachedBouncer used during this time are 'NightClub,' since 2014, and 'Disco,' introduced in 2020 to support data theft, capturing screenshots, recording audio, and more.
.jpg)
MoustachedBouncer campaigns
Source: ESET
AiTM attacks
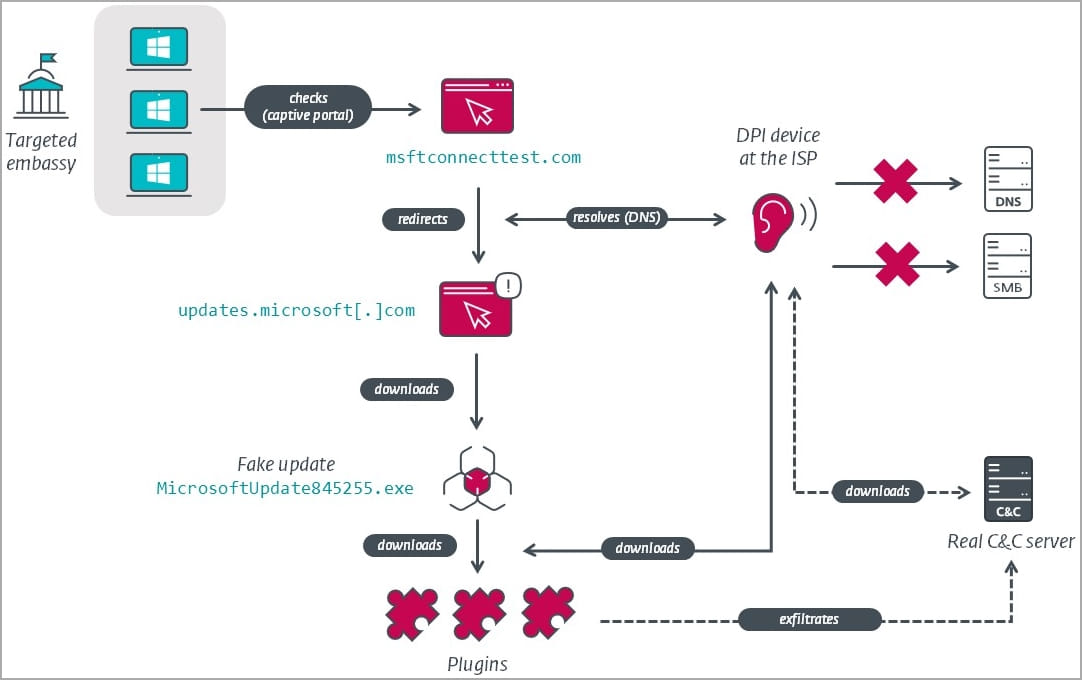
The recent method used to breach networks is to use adversary-in-the-middle (AitM) attacks at the ISP level to trick targeted Windows 10 installation into assuming it stands behind a captive portal.
The ISPs confirmed to be used by MoustachedBouncer are Beltelecom (wholly state-owned) and Unitary Enterprise AI (largest private).
ESET believes the threat actors achieve this by manipulating the traffic either by breaching the ISP infrastructure or collaborating with entities that have access to the network service providers in Belarus.
"For IP ranges targeted by MoustachedBouncer, the network traffic is tampered at the ISP level, and the latter URL redirects to a seemingly legitimate, but fake, Windows Update URL, "updates.microsoft[.]com," explains ESET's report.
"Hence, the fake Windows Update page will be displayed to a potential victim upon network connection."
When a targeted Windows 10 device connects to the network, it will redirect captive portal checks (used to check if a device is connected to the internet) to a Fake Windows update HTML page.
This page uses JavaScript to display a "Get Updates" button that, when clicked, causes a fake operating system update ZIP file to be downloaded.
This ZIP file contains a Go-based malware that creates a scheduled task that executes every minute, fetching another executable, the malware loader, from what appears like a Google Cloud IP address but is likely just there for cover.
The malware payloads the MoustachedBouncer has used since 2014 are various versions of the 'NightClub' and 'Disco' malware toolkits, showcasing notable evolution with each new release.
Observed infection chain
Source: ESET
NightClub malware
NightClub was the first malware framework used by the espionage group, with distinct samples retrieved by ESET's analysts in 2014, 2017, 2020, and 2022.
Early versions featured file monitoring and SMTP (email) exfiltration and command and control server communications, while its authors later added a persistence mechanism and a keylogger,
The latest version of NightClub, used by the hackers between 2020 and 2022, features new modules for taking screenshots, recording audio, keylogging, and setting up a DNS-tunneling backdoor for C2 communications.
The DNS backdoor implements additional commands that give the malware file, directory creation, reading, and searching functions, and process manipulation capabilities.
Also, the newest NightClub uses a hardcoded private RSA-2048 key for encrypting its strings, while its configuration is stored in an external file, giving it more stealth and versatility.
ESET couldn't determine the infection channel that MoustachedBouncer used for NightClub, so that aspect remains unknown.
Disco malware
Disco is a newer malware framework reaching victims through the previously described AitM-based attack chain, which MoustachedBouncer started using in 2020.
Disco uses multiple Go-based plugins that expand its functionality, allowing the malware to:
- Take screenshots every 15 seconds (three modules)
- Execute PowerShell scripts (two modules)
- Exploit CVE-2021-1732 using a publicly-available PoC to elevate privileges
- Set up a reverse proxy using code inspired by the open-source tool 'revsocks' (two modules)
Disco also uses SMB (Server Message Block) shares for data exfiltration, a protocol primarily used for shared access to files, printers, and serial ports, so there's no direct transfer to the C2 server.
MoustachedBouncer's C2 infrastructure is not accessible directly from the public internet, effectively hiding it from security researchers and protecting it from takedowns.
ESET recommends that diplomats and embassy employees based in Belarus use end-to-end encrypted VPN tunnels when accessing the internet to block the AiTM attacks.