Explain me SimpleXChat like i'm five
The SimpleX network protocol (SMP)
It's a protocol (SMP) using relays in a unidirectional way to proxify the P2P activity of users.
It also does content padding (message of random sizes) to make difficult attacks by a inspecting packet size for doing traffic correlation.
Encryption
- Client to Server connections are encrypted in TLS and verified with Ed448.
- Client to Client messages are encrypted in Double Ratchet with Curve448 to agree shared secrets for the double ratchet initialization.
How to use SimpleXChat
1 - Installation
In first, install SimpleXChat | Tor hidden-service.
2 - Launching the app
You need nothing more than launching the app. If you want to share your contact link, click on "Your SimpleX address" and create one.
2.1 Using SimpleXChat over Tor
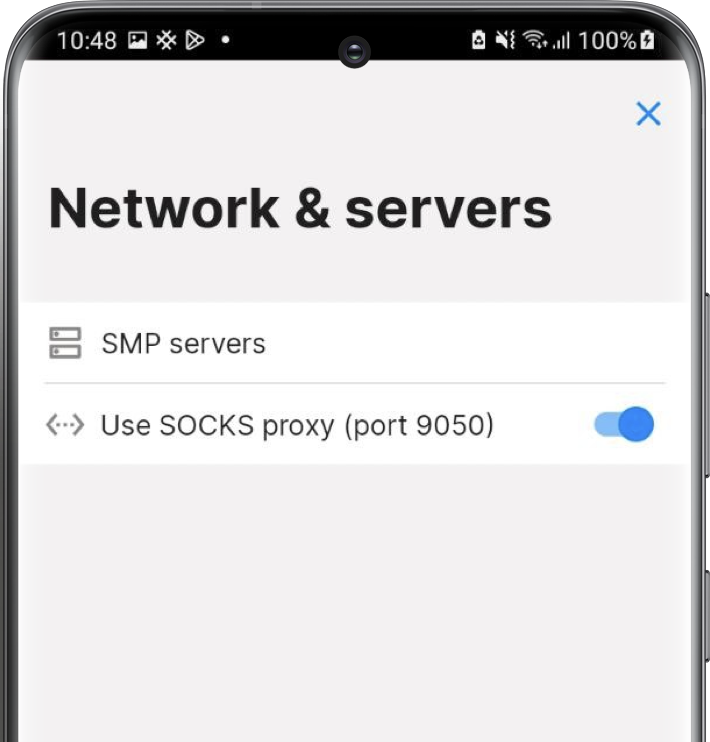
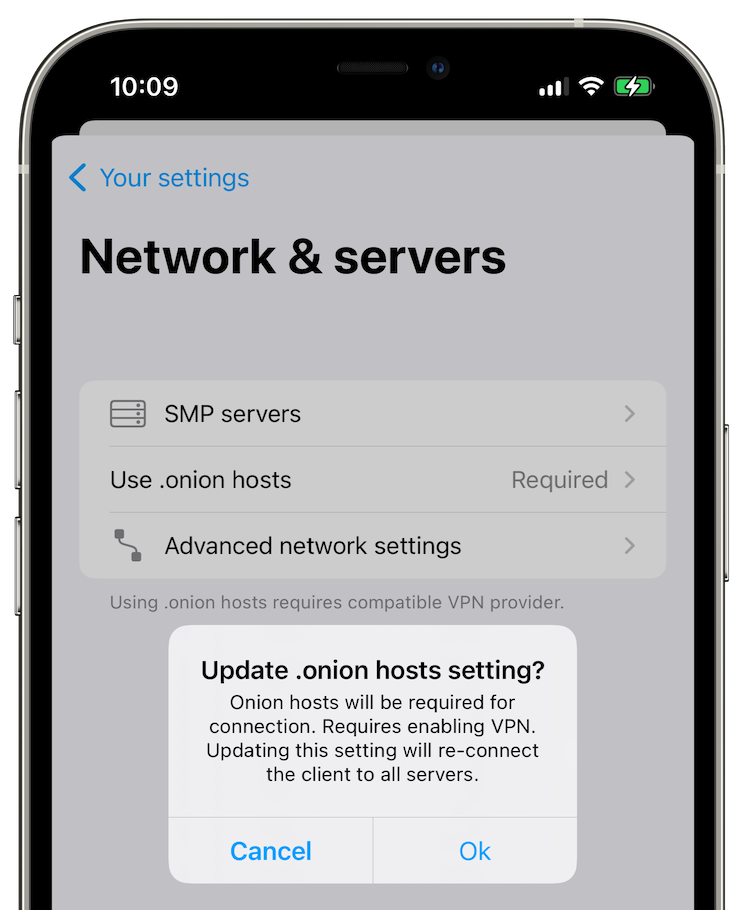
Go in the connection settings and turn-on the Socks proxy switch (be sure you're running Tor in background before activating it.) You also can use hidden-service connection with relays made it available.
3 - Receive messages
Turn on the auto-accept switch if you want to automatically accept message requests and accept incognito if you want to keep a random username per user contacting you. Or click on + and on generate a one-time invitation link to not share your contact address.
4 - Send messages
To contact someone, click on + and on contact via a link or scan a QRCode. Paste it's contact link, for example here's mine
5 - Conversation initialization
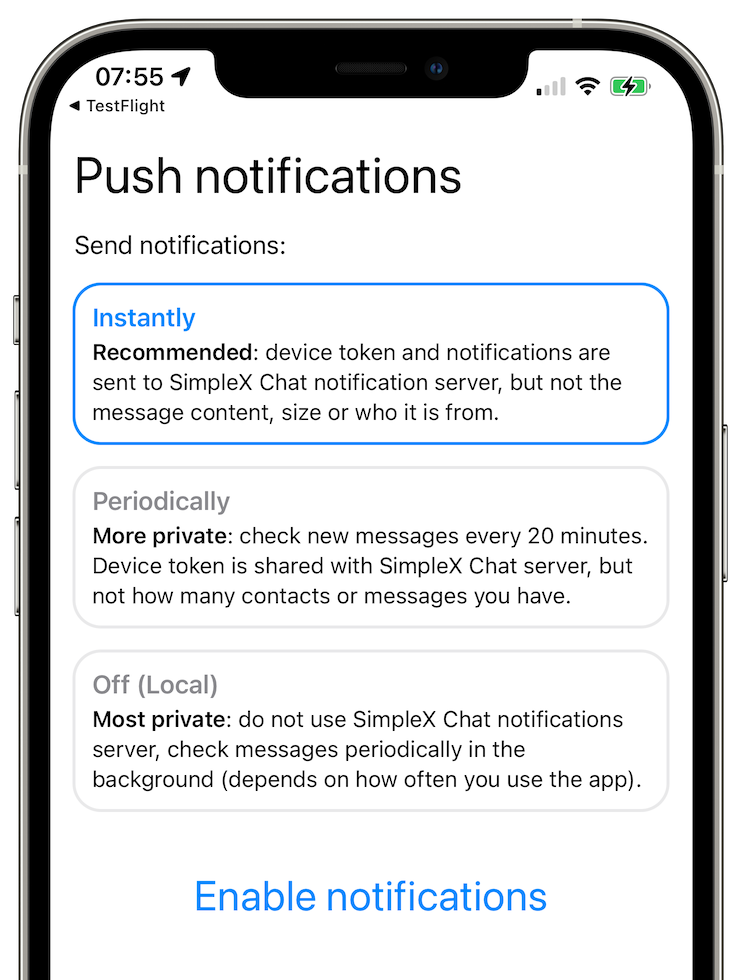
You'll have a connecting... conversation appearing once you create one or when someone is contacting you, during this phase you're doing a key-exchange for double ratchet so make sure you and the other part are online. Why not letting the application running in the background (not on iOS because apple push servers are will know your SimpleX usage, see here why) with the notifications periodically or instantly.
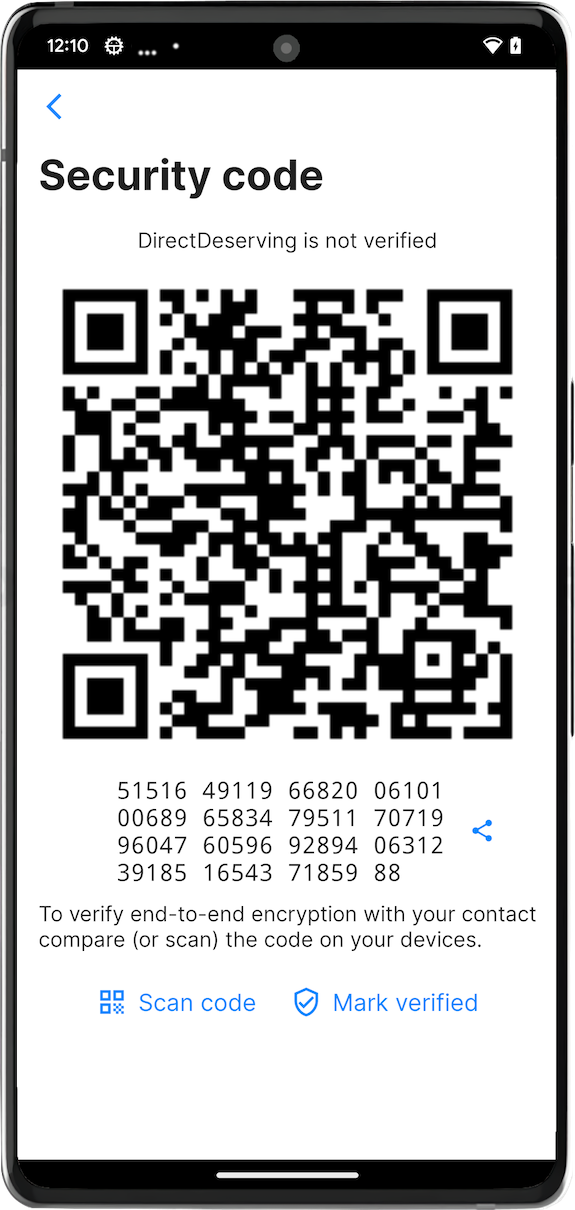
5 - Verify the conversation security
Now the conversation has started, click on the profile of who you're talking, now on verify the security code and verify the fingerprint is the same, with the QRCode or by signing it with your PGP Key as we seen before. Now the conversation is verified, you can talk with the user or setting up an ephemeral conversation in the settings.

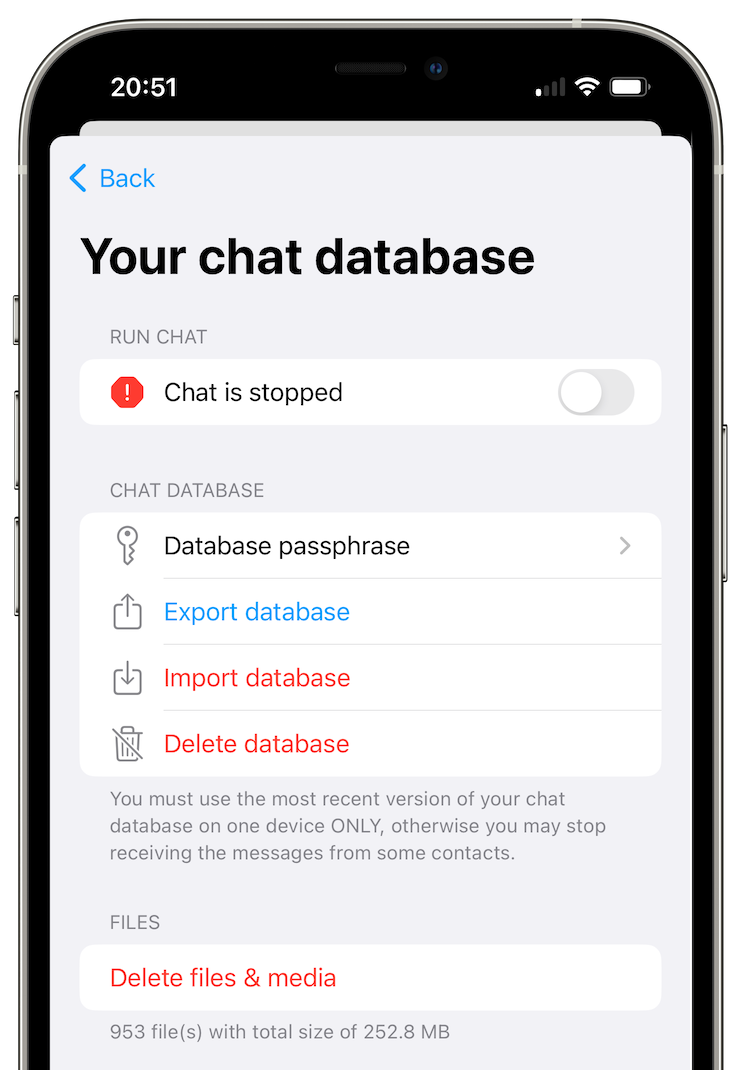
6 - Backup your Database
Conversations are only queued on relays, so you're hosting your own data in a local database. Put the database in pause mode, add a passphrase and export it to the new device where you want to restore it. Beware, you can't have a "multi-device" usage like running the same database on two devices at the same time because of Double Ratchet protection (you "fork" the perfect forwarded secrecy on different sessions)