Got an idea for a new AI-based cybersecurity product? You could win millions in a new contest. Meanwhile, NIST has drafted a major revision to the CSF 2.0 and wants your opinion about it. Also, there’s a new free tool that flags security flaws in public AI models. Plus, most cloud breaches are caused by credential missteps. And much more!
Dive into six things that are top of mind for the week ending August 11.
1 – White House contest to spur development of AI cyber tools
To promote the development of AI-powered cybersecurity products, the White House and the Defense Advanced Research Projects Agency (DARPA) this week unveiled a two-year competition with about $20 million in prizes.
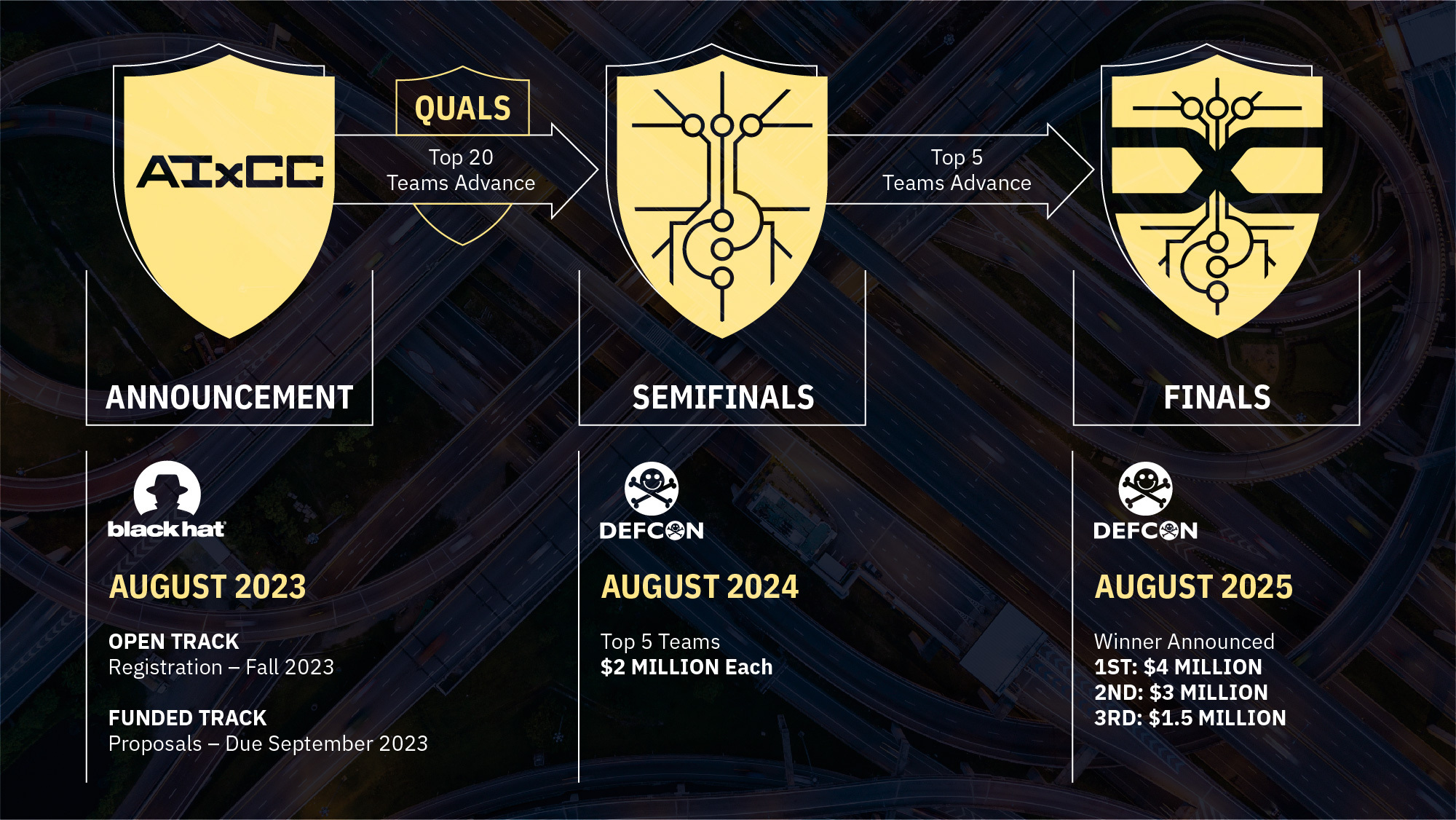
The Artificial Intelligence Cyber Challenge (AIxCC), announced at the Black Hat USA 2023 conference in Las Vegas, is aimed at computer scientists, AI experts, software developers and cybersecurity masters interested in creating next-generation cyber tools that leverage the power of AI.
AI vendors Anthropic, Google, Microsoft and OpenAI will support participants by providing their technology and expertise, while the Open Source Security Foundation (OpenSSF) will act as an advisor.
Small businesses can participate as part of the “funded track,” which will provide monetary support to seven SMBs. All others can enter via the “open track.”
After entrants submit proposals, up to 20 will be selected to participate in a semifinal competition held at DefCon in August 2024. The five teams with the highest scores will be awarded prizes and will move on to the final round at DefCon in August 2025.
“If successful, AIxCC will not only produce the next generation of cybersecurity tools, but will show how AI can be used to better society by defending its critical underpinnings,” Perri Adams, DARPA’s AIxCC program manager, said in a statement.
To get more details, check out the White House’s announcement, DARPA’s announcement, OpenSSF’s announcement and the AIxCC website.
2 – NIST releases Cybersecurity Framework 2.0 draft
The U.S. National Institute of Standards and Technology (NIST) wants you – yes, you! – to comment on the draft of its Cybersecurity Framework 2.0 it released this week.
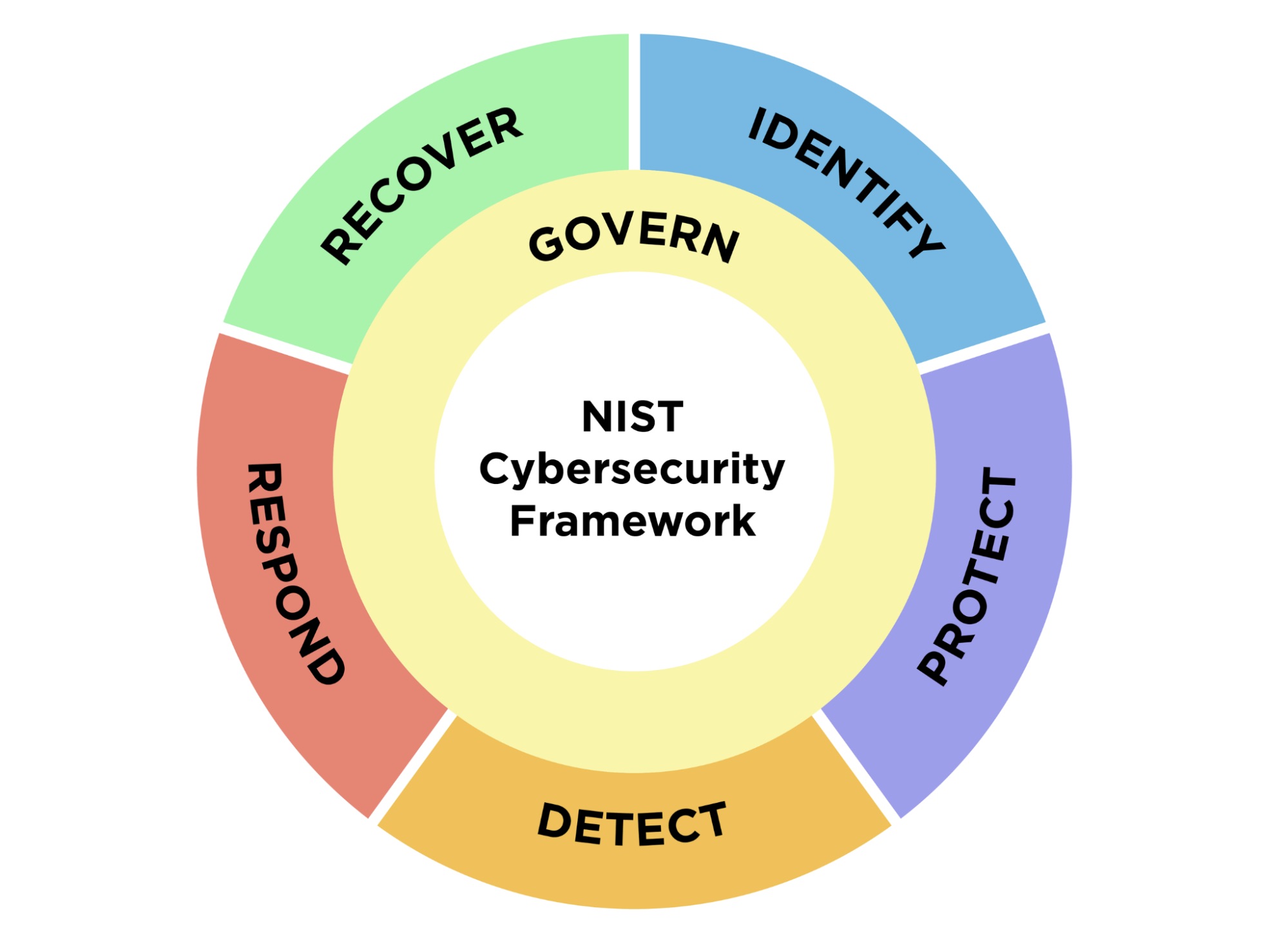
Described as a “major update” to the framework, which was first released in 2014, this draft features an expanded scope, adds a sixth function titled “Govern,” and aims to simplify its implementation through revised guidance.
For example, the framework originally focused specifically on securing U.S. critical infrastructure organizations, but it now aims to encompass all types of organizations worldwide, regardless of size, type and industry sector.
Meanwhile, the new “Govern” function was added to address areas such as risk management strategy, organizational context, cybersecurity supply chain risk management, and policies, processes and procedures.
The five other functions are:
- Identify, focused on assessing an organization’s cyber risk
- Protect, about adopting measures to prevent and reduce cyber risk
- Detect, centered on discovering and analyzing cyberattacks and breaches
- Respond, devoted to taking action after a cyber incident
- Recover, focused on the restoration of impacted assets and operations
“The NIST Cybersecurity Framework (Framework or CSF) 2.0 provides guidance for reducing cybersecurity risks by helping organizations to understand, assess, prioritize, and communicate about those risks and the actions that will reduce them,” the draft document reads.
Care to share your feedback on this CSF 2.0 draft with NIST? You can email your comments to [email protected] until Nov. 4, 2023. NIST is particularly interested in hearing whether the public thinks this draft addresses current and anticipated cybersecurity challenges, and aligns with established practices and guidance.
NIST expects to publish the final version of the CSF 2.0 in early 2024, at which point it will officially replace CSF 1.1, released in 2018.
To get more details, check out the CSF’s homepage, NIST’s announcement, a draft summary and the full 52-page draft document.
3 – Open source tool detects supply chain risks in AI models
Is your organization using an artificial intelligence model it pulled from a public repository? Are you sure it’s secure? If not, you might want to check out a new and free open-source tool designed to flag supply-chain vulnerabilities and risks in publicly available AI models.
The AI Risk Database was created in March by AI vendor Robust Intelligence, which then collaborated with MITRE to further refine it into the version unveiled this week on GitHub. Indiana University is also part of the collaboration.
“This collaboration and release of the AI Risk Database can directly enable more organizations to see for themselves how they are directly at risk and vulnerable in deploying specific types of AI-enabled systems,” Douglas Robbins, MITRE vice president of engineering and prototyping, said in a statement.

Representatives from the three organizations talked about the AI Risk Database in a pair of presentations at Black Hat USA 2023 in Las Vegas.
To get more details, check out the announcement from MITRE and Robust Intelligence.
For more information about using AI for cybersecurity, check out these Tenable resources:
How Generative AI is Changing Security Research: The Development of the G-3PO Tool
4 – Google: Most cloud breaches due to credential failures
Weak or non-existent passwords, along with leaked credentials accounted for about 62% of cloud compromises observed by Google Cloud incident response teams in the first quarter of 2023.
Enterprises impacted by this “consistent challenge” could address it by beefing up their identity management wares and processes, Google said in the “August 2023 Threat Horizons Report” from its Cybersecurity Action Team.
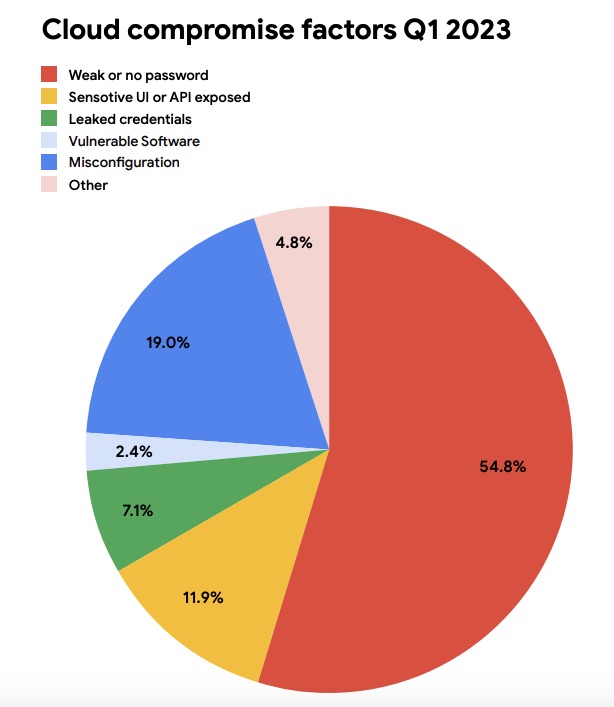
(Source: “August 2023 Threat Horizons Report” from Google’s Cybersecurity Action Team)
Other findings from the 31-page report include:
- Cyber crooks are getting legit-looking Android applications approved in the Google Play Store, and then are adding malicious features to them via stealthy versioning updates done through unapproved channels. Enterprise mitigations for this type of threat include:
- Adopt an enterprise mobility management system
- Create lists of pre-approved applications for your users
- According to an analysis of anonymized alert statistics from Google’s Chronicle Security Operations, the top risk action that can lead to compromises was, by far, cross-project abuse of Google Cloud Platform’s access token generation permission
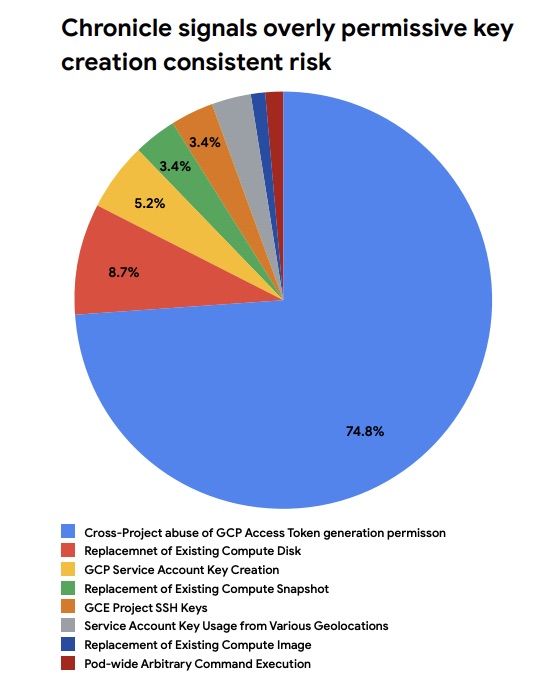
(Source: “August 2023 Threat Horizons Report” from Google’s Cybersecurity Action Team)
To get all the details, read the full report.
For more information about identity and access management security:
5 – CISA issues cybersecurity strategic plan
Cyberbreaches have become rare. Organizations are secure and can withstand cyberattacks. Tech products are inherently secure.
These statements aren’t true today, but the U.S. Cybersecurity and Infrastructure Security Agency (CISA) wants to make them a reality, as stated in its newly released Cybersecurity Strategic Plan.
“We must be clear-eyed about the future we seek, one in which damaging cyber intrusions are a shocking anomaly, in which organizations are secure and resilient, in which technology products are safe and secure by design and default,” reads the document.

The plan, which outlines CISA’s cybersecurity mission for the next three years, establishes three main goals:
- Address immediate threats by:
- improving visibility into and mitigations of cyberthreats
- coordinating disclosures, hunts and mitigations of critical vulnerabilities
- Planning and executing cyberdefense operations and incident response
- Harden the terrain by:
- understanding how attacks occur and how to stop them
- driving effective cybersecurity investments
- filling gaps in cybersecurity services
- Drive security at scale by:
- promoting the development of secure tech products
- understanding and reducing emerging technologies’ cyber risks
- helping to build a cyber workforce
To get all the details, check out CISA’s announcement and the full plan document.
For more information:
6 – Biden seeks to limit U.S. investments in Chinese AI
Citing national security concerns, the Biden administration this week issued an executive order to regulate U.S. technology investments in certain “countries of concern,” including China, in areas including artificial intelligence, microelectronics and quantum computing.
The executive order calls for the creation of a national security program that the Treasury Department will be tasked with implementing and managing.

“This program will seek to prevent foreign countries of concern from exploiting U.S. investment in this narrow set of technologies that are critical to support their development of military, intelligence, surveillance, and cyber-enabled capabilities that risk U.S. national security,” reads the White House announcement.
The Treasury Department is now in the process of gathering public feedback to help it craft the rules of this executive order’s program. Draft regulations will be released at a later date.
For more information, check out: