New HiatusRAT malware attacks target US Defense Department

In a new HiatusRAT malware campaign, threat actors have targeted a server belonging to the U.S. Department of Defense in what researchers described as a reconnaissance attack.
This is a significant shift in tactics, seeing that the attacks previously focused on organizations from Latin America and Europe, being deployed to compromise business-class DrayTek Vigor VPN routers used by medium-sized businesses for remotely connecting to corporate networks.
However, as Lumen's Black Lotus Labs observed, the campaign's reconnaissance efforts took an unexpected turn between mid-June through August. A U.S. military procurement system was also targeted, with Taiwan-based organizations also singled out.
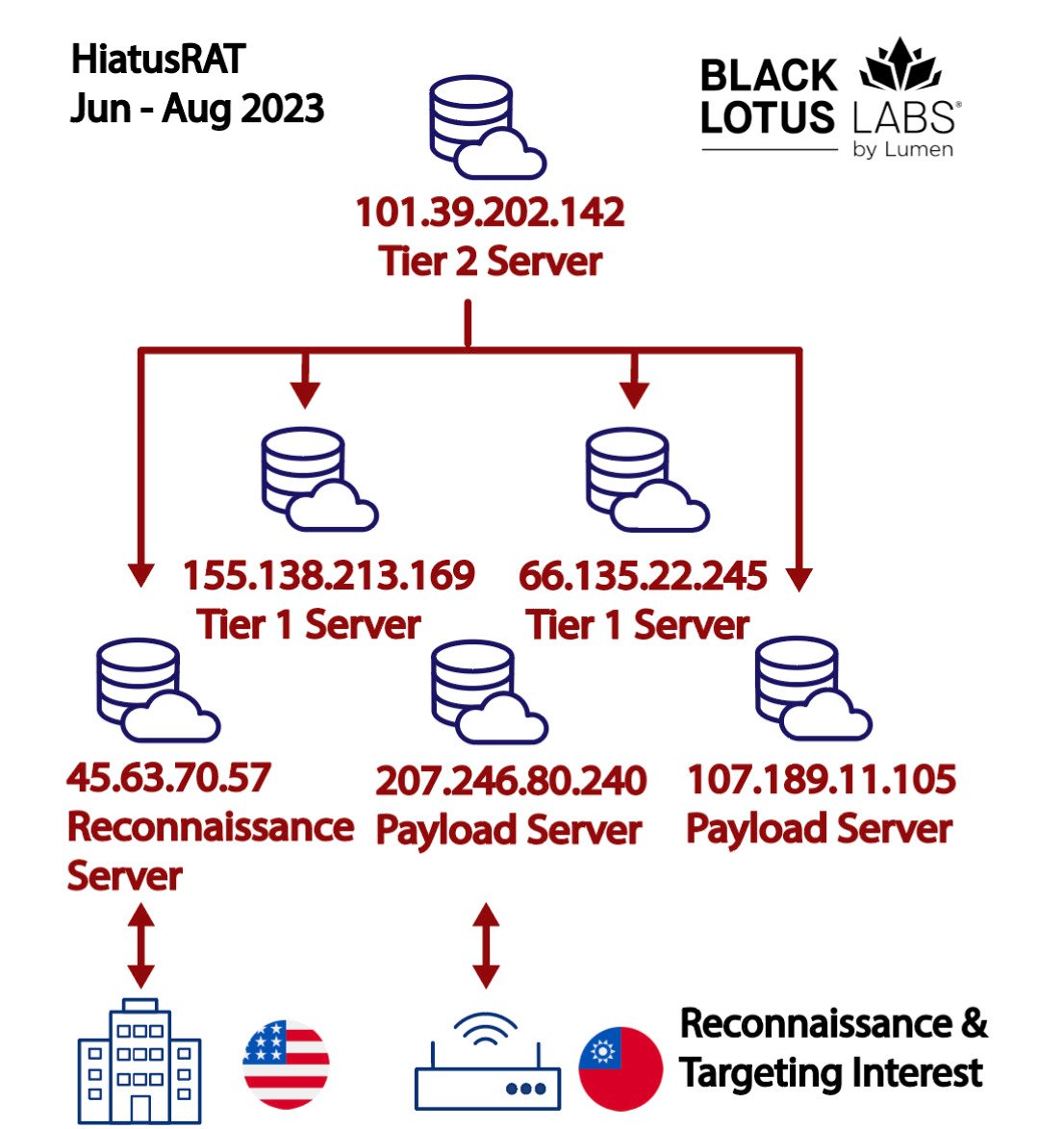
HiatusRAT samples were recompiled to cater to various architectures ranging from Arm, Intel 80386, and x86-64 to MIPS, MIPS64, and i386) and hosted on newly acquired virtual private servers (VPSs).
One of these VPS nodes was used in a data transfer operation with a U.S. military server designated for contract proposals and submissions.
The website's affiliation with contract proposals suggests that the attackers might be seeking publicly accessible information about military requisites or trying to find information on Defense Industrial Base (DIB)-affiliated organizations.
"We suspect this actor was searching for publicly available resources related to current and future military contracts," Lumen's Black Lotus Labs said.
"Given that this website was associated with contract proposals, we suspect the objective was to obtain publicly available information about military requirements and searching for organizations involved in the Defense Industrial Base (DIB), potentially for subsequent targeting."
New HiatusRAT campaign (Lumen Black Lotus Labs)
This campaign follows an earlier series of attacks where over a hundred businesses, mainly from Europe, North America, and South America, were infected with HiatusRAT to create a covert proxy network.
The malware is primarily used to install additional payloads on infected devices and convert the compromised systems into SOCKS5 proxies for command and control server communication.
"Despite prior disclosures of tools and capabilities, the threat actor took the most minor of steps to swap out existing payload servers and carried on with their operations, without even attempting to re-configure their C2 infrastructure," Lumen said.
As Lumen highlights, this shift in information collection and targeting preferences aligns with Chinese strategic interests, a connection emphasized by the 2023 ODNI annual threat assessment.
U.S. organizations have also been recently targeted in attacks linked to other Chinese-backed threat groups, including Volt Typhoon and Storm-0558.
"We suspect the HiatusRAT cluster serves as another example of tradecraft that could be applied against the U.S. Defense Industrial Base with a sense of impunity. We recommend defense contractors exercise caution and monitor their networking devices for the presence of HiatusRAT," Lumen concluded.