Google released first quantum-resilient FIDO2 key implementation

Google has announced the first open-source quantum resilient FIDO2 security key implementation, which uses a unique ECC/Dilithium hybrid signature schema co-created with ETH Zurich.
FIDO2 is the second major version of the Fast IDentity Online authentication standard, and FIDO2 keys are used for passwordless authentication and as a multi-factor authentication (MFA) element.
Google explains that a quantum-resistant FIDO2 security key implementation is a crucial step towards ensuring safety and security as the advent of quantum computing approaches and developments in the field follow an accelerating trajectory.
"As progress toward practical quantum computers is accelerating, preparing for their advent is becoming a more pressing issue as time passes," explains Google.
"In particular, standard public key cryptography, which was designed to protect against traditional computers, will not be able to withstand quantum attacks."
With quantum computers being actively developed, there is concern that they will soon be used to more efficiently and quickly crack encryption keys, making encrypted information accessible to governments, threat actors, and researchers.
To protect against quantum computers, a new hybrid algorithm was created by combining the established ECDSA algorithm with the Dilithium algorithm.
Dilithium is a quantum-resistant cryptographic signature scheme that NIST included in its post-quantum cryptography standardization proposals, praising its strong security and excellent performance, making it suitable for use in a wide array of applications.
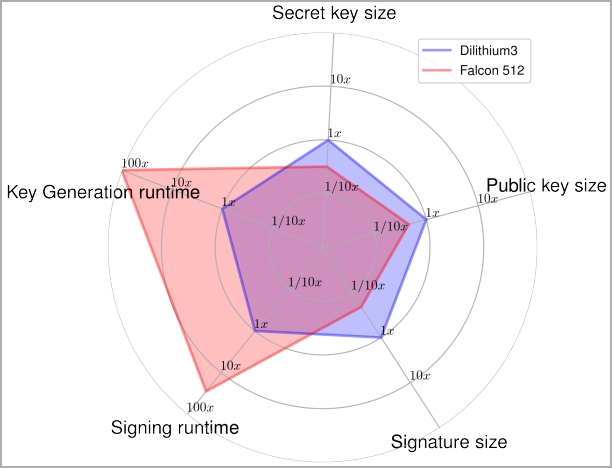
Comparison of performance and size of quantum-resistant schemes
(eprint.iacr.org)
This hybrid signature approach that blends classic and quantum-resistant features wasn't simple to manifest, Google says. Designing a Dilithium implementation that's compact enough for security keys was incredibly challenging.
Its engineers, however, managed to develop a Rust-based implementation that only needs 20KB of memory, making the endeavor practically possible, while they also noted its high-performance potential.
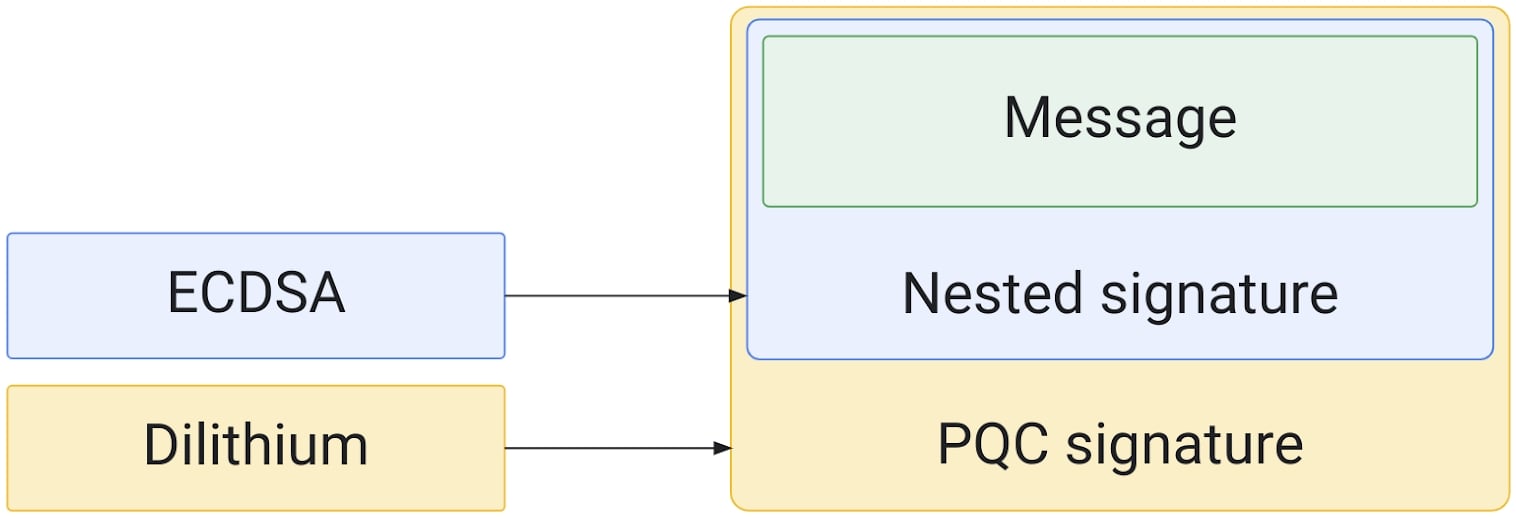
The hybrid signature schema was first presented in a 2022 paper and recently gained recognition at the ACNS (Applied Cryptography and Network Security) 2023, where it won the "best workshop paper" award.
This new hybrid implementation is now part of the OpenSK, Google's open-source security keys implementation that supports the FIDO U2F and FIDO2 standards.
The tech giant hopes that its proposal will be adopted by FIDO2 as a new standard and supported by major web browsers with large user bases.
The firm calls the application of next-gen cryptography at the internet scale "a massive undertaking" and urges all stakeholders to move quickly to maintain good progress on that front.
Last week, Google introduced a quantum-resistant hybrid cryptography mechanism called X25519Kyber768 in Chrome 116, which encrypts TLS connections.
This move came in anticipation of the risk of future quantum computers having the capacity to decrypt today's data, addressing the "Harvest Now, Decrypt Later" threat.