Ivanti Avalanche impacted by critical pre-auth stack buffer overflows

Two stack-based buffer overflows collectively tracked as CVE-2023-32560 impact Ivanti Avalanche, an enterprise mobility management (EMM) solution designed to manage, monitor, and secure a wide range of mobile devices.
The flaws are rated critical (CVSS v3: 9.8) and are remotely exploitable without user authentication, potentially allowing attackers to execute arbitrary code on the target system.
The vulnerability impacts WLAvalancheService.exe version 6.4.0.0 and older, which receives communications over TCP port 1777.
An attacker sending specially crafted data packets containing hex strings (type 3) or a list of decimal strings separated by “;” (type 9) can cause a buffer overflow due to a fixed-size stack-based buffer used to store the converted data.
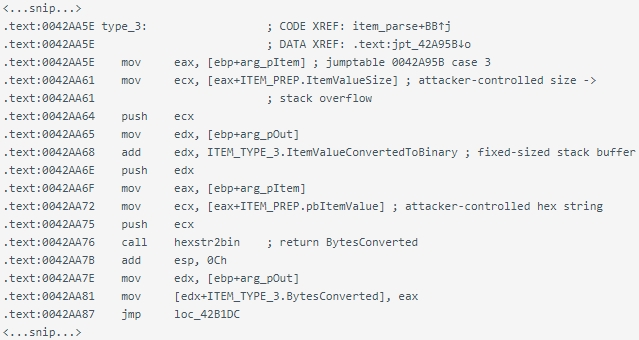
Code snippet that showcases the buffer overflow vulnerability (Tenable)
Buffer overflow is a type of security problem where a program writes more data to an adjacent memory block (buffer) than it can hold, overwriting those locations and causing program crashes or arbitrary code execution.
Stack-based buffer overflows concern the overwrite of regions allocated on the stack, a memory region that stores the program’s local variables and return addresses, making it possible to direct the program to execute malicious code.
The issues were discovered by Tenable researchers and reported to Ivanti on April 4, 2023, while a proof-of-concept was shared with the vendor on April 13, 2023.
After extending the disclosure window to allow the vendor more time to address the issues, a security update was released on August 3, 2023, with Avalanche version 6.4.1.
Along with CVE-2023-32560, Avalanche version 6.4.1 also fixes CVE-2023-32561, CVE-2023-32562, CVE-2023-32563, CVE-2023-32564, CVE-2023-32565, and CVE-2023-32566, concerning various authentication bypass and remote code execution flaws.
Ivanti software is used in critical systems and settings, so threat actors are constantly looking for critical-severity vulnerabilities that constitute potential gateways for attacks.
Last month, it was revealed that hackers exploited a zero-day authentication bypass vulnerability (CVE-2023-35078) in Ivanti Endpoint Manager Mobile (EPMM) to breach a platform used by twelve ministries of the Norwegian government, accessing potentially sensitive and classified information.