Comedy Heaven
So bad it's ascended.
For comedy that's so bad it's good.
Unsure if your post fits our community? See our guide.
Partnered communities:
Rules:
-
Follow Comedy Heaven's posting guidelines. In short, images should be ironically funny, but originally intended unironically or passable as such.
-
Follow Lemmy's Code of Conduct. No form of discrimination or hate will be tolerated.
-
Follow lemmy.world's Code of Conduct. This community is hosted on lemmy.world, and therefore must abide its rules (and mastodon.world's rules by extension).
-
Tag posts as NSFW if they are sexual in nature. If you are unsure, err on the safe side.
-
No politics. This is not a place for serious discussion, debate, or argument.
-
No violence or gore.
-
No set of rules is exhaustive. The mods reserve the right to update or expand this list in order to maintain an inviting and on-topic space.
view the rest of the comments
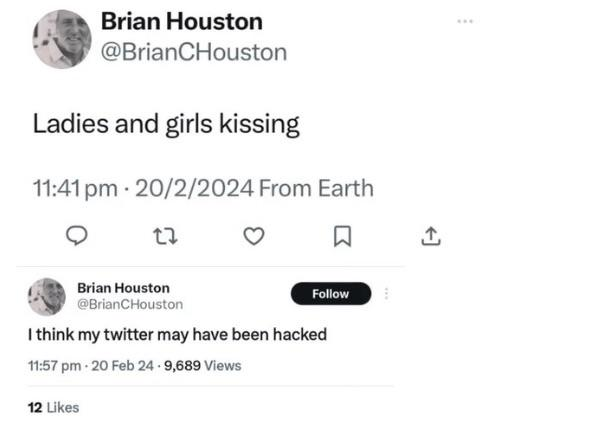
Tell me you don't work on or around security without telling me. The gist is correct though
I'm a CS student
"most hacker attacks are phishing attacks", while phishing is prevelant, password guessing and spraying campaigns are far more common. I can show you the logs where we get thousands of login attempts daily, we don't receive anywhere near that volume of phishing attempts. Obviously hacking isn't just "breaching a systems firewall". What does that even mean? Reverse shells are incredibly common to bypass inbound firewall rules. "decrypting passwords", I assume you mean cracking the hash. Passwords are not stored encrypted.