The War Room
Community for various OSINT news and subject matter for open discussion or dissemination elsewhere
Malicious extensions can abuse VS Code flaw to steal auth tokens

Microsoft's Visual Studio Code (VS Code) code editor and development environment contains a flaw that allows malicious extensions to retrieve authentication tokens stored in Windows, Linux, and macOS credential managers.
These tokens are used for integrating with various third-party services and APIs, such as Git, GitHub, and other coding platforms, so stealing them could have significant consequences for a compromised organization's data security, potentially leading to unauthorized system access, data breaches, etc.
The flaw was discovered by Cycode researchers, who reported it to Microsoft along with a working proof-of-concept (PoC) they developed. Yet, the tech giant decided against fixing the issue, as extensions are not expected to be sandboxed from the rest of the environment.
Stealing secrets with extensions
The security problem discovered by Cycode is caused by a lack of isolation of authentication tokens in VS Code's 'Secret Storage,' an API that allows extensions to store authentication tokens in the operating system. This is done using Keytar, VS Code's wrapper for communication with the Windows credential manager (on Windows), keychain (on macOS), or keyring (for Linux).
This means that any extension running in VS Code, even malicious ones, can gain access to the Secret Storage and abuse Keytar to retrieve any stored tokens.
Keychain containing login passwords
Source: Cycode
Upon discovering the problem, Cycode's researchers started experimenting by creating a malicious extension to steal tokens for CircleCI, a popular coding platform with VS Code extensions. They did this by modifying CircleCI's extension to run a command that would expose its secure token and even send it straight to the researcher's server.
Gradually, they developed a more versatile attack method to extract those secrets without tampering with the target extension's code.
The key to this process was discovering that any VS Code extension is authorized to access the keychain because it runs from within the application that the operating system has already granted access to the keychain.
"We developed a proof-of-concept malicious extension that successfully retrieved tokens not only from other extensions but also from VS Code's built-in login and sync functionality for GitHub and Microsoft accounts, presenting a "Token Stealing” attack." - Cycode.
Next, the retrieved tokens had to be decrypted, and Cycode found that the algorithm used to encrypt tokens was AES-256-GCM, which is usually safe. However, the key used to encrypt the tokens was derived from the current executable path and the machine ID, making it easy to recreate the key.
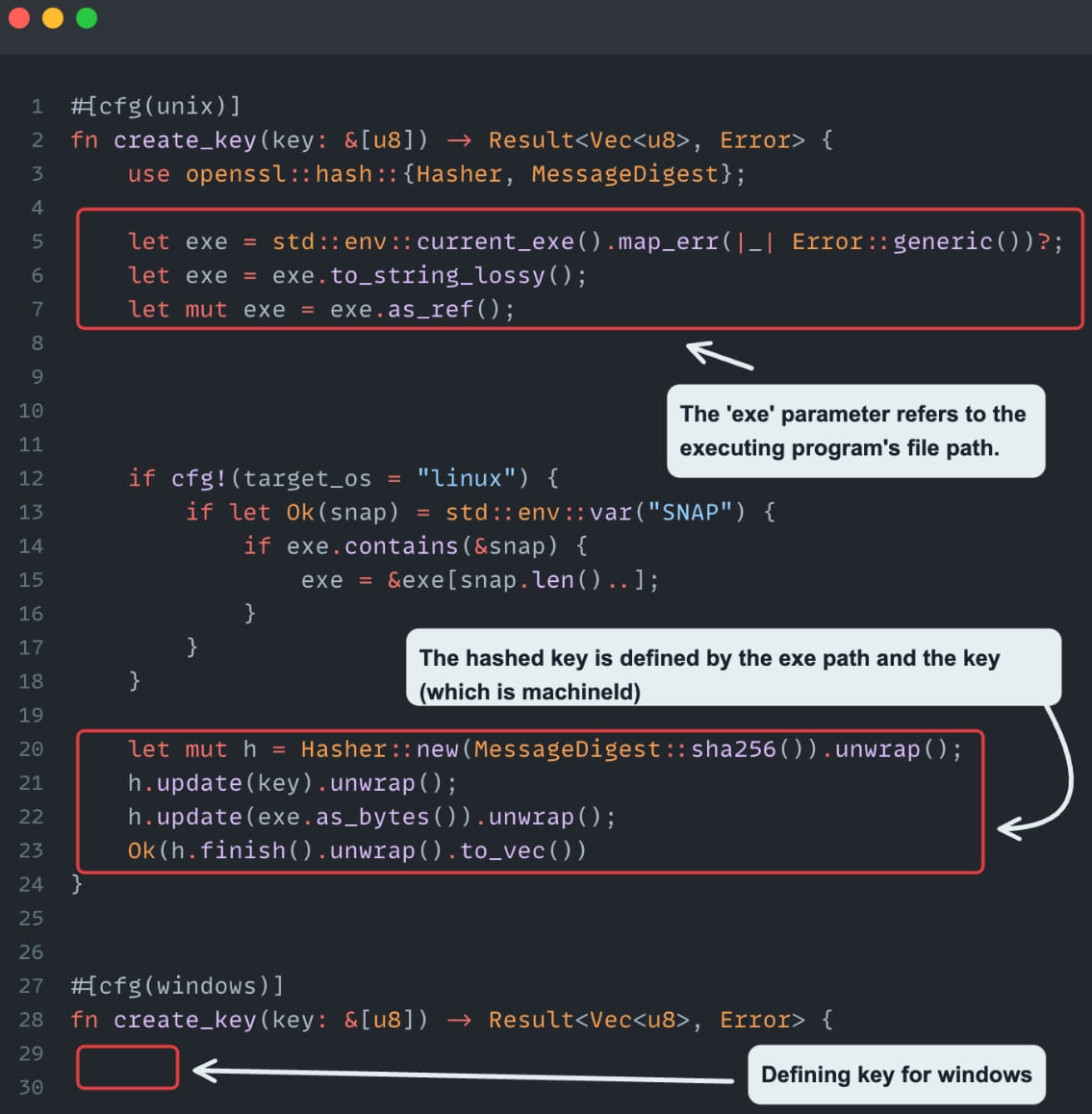
Info that helps decrypt secrets
Source: Cycode
The retrieved tokens were decrypted by a custom JS script run in VS Code's Electron executable, deciphering and printing all passwords of locally installed extensions.
Decrypting the retrieved tokens
Source: Cycode
A second flaw discovered by Cycode's researchers was that the 'getFullKey' function retrieves secrets by a given 'extensionId,' which is derived from the extension's name and publisher.
This problem allows anyone to modify these fields and trick VS Code into granting them access to another extension's secure tokens.
Cycode tested this using a PoC extension that mimicked CircleCI again; however, they noted that replicating any other extension and gaining access to its secrets would be trivial.
<iframe allowfullscreen frameborder="0" height="360" mozallowfullscreen src="https://player.vimeo.com/video/849064860" webkitallowfullscreen width="640">
Disclosure and (not) fixing
Cycode's analysts disclosed the problem to Microsoft two months ago, even demonstrating their PoC extension and its ability to steal stored extension tokens.
Regardless, Microsoft's engineers didn't see this as a security concern and decided to maintain the existing design of VS Code's secret storage management framework.
BleepingComputer has contacted Microsoft for a comment on the above but has not received a response to our questions.
Microsoft Office update breaks actively exploited RCE attack chain

Microsoft today released a defense-in-depth update for Microsoft Office that prevents exploitation of a remote code execution (RCE) vulnerability tracked as CVE-2023-36884 that threat actors have already leveraged in attacks.
In today's Microsoft August Patch Tuesday, the update helps fix CVE-2023-36884, a security issue disclosed in July, which Microsoft did not patch at the time but provided mitigation advice.
Initially, the bug was reported as an RCE in Microsoft Office, but further review led to classifying it as a Windows Search remote code execution.
Hackers exploited the vulnerability as a zero-day to execute code remotely using malicious Microsoft Office documents in attacks from the RomCom threat group for financial and espionage purposes.
Enhanced security to stop RCE
In an advisory today, Microsoft refers to the Office update as one "that provides enhanced security as a defense in depth measure."
Additional information from the company explains that the update is designed to stop the attack chain that triggers CVE-2023-36884.
Microsoft recommends installing the Office updates released today as well as Windows updates from this month.
In the original advisory, Microsoft explains that an attacker could exploit the vulnerability by sending a specially crafted file over email or message communication.
Although user interaction is required, threat actors could easily come up with a sufficiently convincing bait and lure the potential victim into opening the malicious file.
As per Microsoft's assessment, successful exploitation could lead to high loss of confidentiality, integrity, and availability, meaning that an attacker could drop a malicious file evading Mark of the Web (MoTW) defenses and provide code execution on the compromised system.
Today's Office updates for stopping exploitation of the Windows Search security bypass vulnerability identified as CVE-2023-36884 are available for the Microsoft Office 2013/2016/2019 suite and apps for both 32-bit and 64-bit architectures.
The severity level for the update has been assessed to be a moderate one.
Judge Gives MindGeek ‘Pirate’ Domains After Porn Pirate Violates Injunction
In 2022, MindGeek subsidiary MG Premium prevailed in its legal battle against the operator of Daftsex and several other pirate sites. MG was awarded $32m in damages and permission to seize domain names but to date, nothing has been paid, and the sites are still in business. Mindful that his injunction is being ignored, a U.S. judge has just held the persistent pirate in contempt of court and declared MG Premium the new owner of his pirate domains.
From: TF, for the latest news on copyright battles, piracy and more.
Patch Tuesday: Microsoft (Finally) Patches Exploited Office Zero-Days
Patch Tuesday: A month after confirming active exploitation of Office code execution flaws, Microsoft has shipped patches for multiple affected products.
The post Patch Tuesday: Microsoft (Finally) Patches Exploited Office Zero-Days appeared first on SecurityWeek.
What Cisco Talos knows about the Rhysida ransomware
Cisco Talos is aware of the recent advisory published by the U.S. Department of Health and Human Services (HHS) warning the healthcare industry about Rhysida ransomware activity.
As we've discussed recently, there has been huge growth in the ransomware and extortion space, potentially linked to the plethora
Six critical vulnerabilities included in August’s Microsoft security update
The only vulnerability Microsoft states is being exploited in the wild is CVE-2023-38180, a denial-of-service vulnerability in .NET and Microsoft Visual Studio.
UK Electoral Commission Admits Major Data Breach Spanning Over a Year
The compromised electoral registers contained information from 2014 to 2022, including the names and addresses of voters, both domestic and overseas.
This is a post from HackRead.com Read the original post: UK Electoral Commission Admits Major Data Breach Spanning Over a Year
Google’s Messages app will now use RCS by default and encrypt group chats
Google announced today it’s making its Messages by Google app more secure with improvements to RCS, or Rich Communication Services — a protocol aimed at replacing SMS and is more on par with the advanced features found in Apple’s iMessage. The company says it will now make RCS the default for both new and existing […]
Microsoft’s August 2023 Patch Tuesday Addresses 73 CVEs (CVE-2023-38180)
Microsoft addresses 73 CVEs, including one vulnerability exploited in the wild.
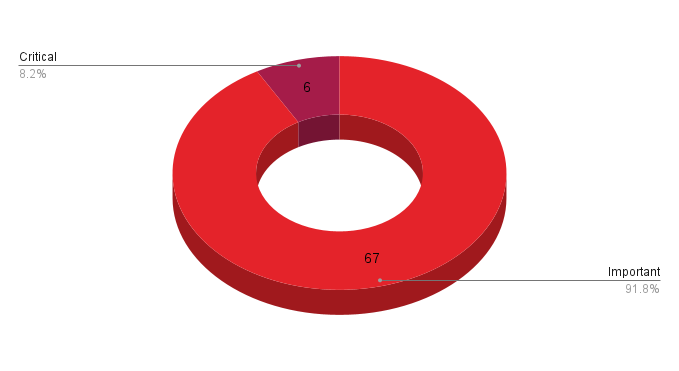
- 6Critical
- 67Important
- 0Moderate
- 0Low
Microsoft patched 73 CVEs in its August Patch Tuesday release, with six rated as critical and 67 rated as important. Microsoft also released two advisories (ADV230003 and ADV230004) this month as well as a patch for a vulnerability in AMD processors (CVE-2023-20569). These were omitted from our totals.
This month’s update includes patches for:
- .NET Core
- .NET Framework
- ASP.NET
- ASP.NET and Visual Studio
- Azure Arc
- Azure DevOps
- Azure HDInsights
- Dynamics Business Central Control
- Memory Integrity System Readiness Scan Tool
- Microsoft Dynamics
- Microsoft Exchange Server
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Teams
- Microsoft WDAC OLE DB provider for SQL
- Microsoft Windows Codecs Library
- Reliability Analysis Metrics Calculation Engine
- Role: Windows Hyper-V
- SQL Server
- Tablet Windows User Interface
- Windows Bluetooth A2DP driver
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows Cryptographic Services
- Windows Defender
- Windows Fax and Scan Service
- Windows Group Policy
- Windows HTML Platform
- Windows Kernel
- Windows LDAP - Lightweight Directory Access Protocol
- Windows Message Queuing
- Windows Mobile Device Management
- Windows Projected File System
- Windows Reliability Analysis Metrics Calculation Engine
- Windows Smart Card
- Windows System Assessment Tool
- Windows Wireless Wide Area Network Service
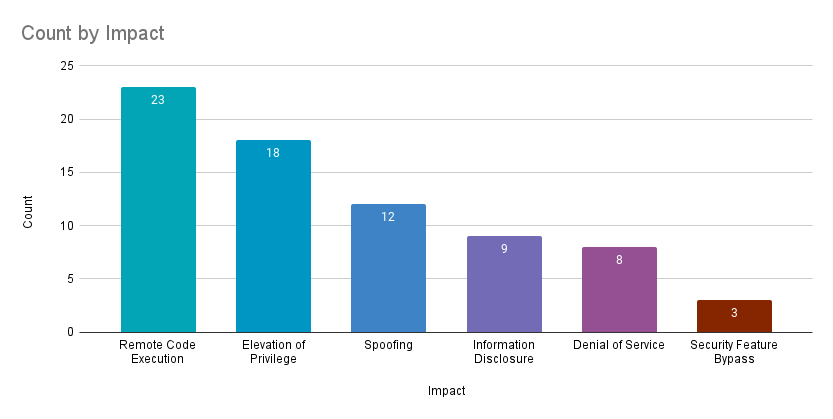
Remote code execution (RCE) vulnerabilities accounted for 31.5% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 24.7%.
Important
CVE-2023-38180 |.NET and Visual Studio Denial of Service Vulnerability
CVE-2023-38180 is a Denial of Service (DoS) vulnerability in Microsoft Visual Studio,.NET versions 6.0 and 7.0, and ASP.NET Core 2.1. It is rated as “Important” and was assigned a CVSSv3 score of 7.5. According to Microsoft, this vulnerability was exploited in the wild as a zero-day. While details of its exploitation were not available at the time this blog post was published, an attacker that exploits this vulnerability would be able to create a DoS condition on a vulnerable server.
Critical
CVE-2023-35385, CVE-2023-36910 and CVE-2023-36911 | Microsoft Message Queuing Remote Code Execution Vulnerability
CVE-2023-35385, CVE-2023-36910 and CVE-2023-36911 are RCE vulnerabilities in the Microsoft Message Queuing (MSMQ) component of Windows operating systems that were each given a CVSSv3 score of 9.8 and a rating of critical. Microsoft rated these vulnerabilities as “Exploitation Less Likely” using the Microsoft Exploitability Index.
A remote unauthenticated attacker can exploit this vulnerability by sending malicious MSMQ packets to a vulnerable MSMQ server leading to arbitrary code execution. However, in order to exploit this flaw, the Message Queuing service needs to be enabled on the vulnerable server. Microsoft says if the service is enabled, it runs under the service name “Message Queuing” and is listening on TCP port 1801. Tenable customers can utilize Plugin ID 174933 to identify systems that have this service running.
Yuki Chen, a security researcher with Cyber KunLun, is credited with discovering a total of six vulnerabilities in Microsoft Message Queuing in August 2023, including the three above as well as two DoS vulnerabilities (CVE-2023-36912 and CVE-2023-38172) and CVE-2023-35383, an information disclosure vulnerability.
Important
CVE-2023-21709 | Microsoft Exchange Server Elevation of Privilege Vulnerability
CVE-2023-21709 is an EoP vulnerability in Microsoft Exchange Server. It was assigned a CVSSv3 score of 9.8 and is rated as Exploitation Less Likely. An unauthenticated attacker could exploit this vulnerability by attempting to brute force the password for valid user accounts. Successful exploitation would allow an attacker to “login as another user.”
According to the advisory, additional steps are required in order to address this vulnerability. After applying the patch, a PowerShell script must be run. We recommend reviewing the advisory for the latest information from Microsoft to successfully remediate this vulnerability.
This is the third EoP vulnerability in Microsoft Exchange Server disclosed in 2023. The first two were disclosed as part of the January 2023 Patch Tuesday release (CVE-2023-21763, CVE-2023-21764).
Important
CVE-2023-38181, CVE-2023-38185, CVE-2023-35368, CVE-2023-38182, CVE-2023-35388 | Additional Microsoft Exchange Server Vulnerabilities
In addition to CVE-2023-21709, Microsoft patched five other vulnerabilities in Microsoft Exchange Server:
| CVE | Title | CVSSv3 | Exploitability |
|---|---|---|---|
| CVE-2023-38181 | Microsoft Exchange Server Spoofing Vulnerability | 8.8 | Exploitation Less Likely |
| CVE-2023-38185 | Microsoft Exchange Server Remote Code Execution Vulnerability | 8.8 | Exploitation Less Likely |
| CVE-2023-35368 | Microsoft Exchange Server Remote Code Execution Vulnerability | 8.8 | Exploitation Less Likely |
| CVE-2023-38182 | Microsoft Exchange Server Remote Code Execution Vulnerability | 8.0 | Exploitation More Likely |
| CVE-2023-35388 | Microsoft Exchange Server Remote Code Execution Vulnerability | 8.0 | Exploitation More Likely |
Of the five other vulnerabilities patched this month, two (CVE-2023-38182, CVE-2023-35388) are rated as “Exploitation More Likely.” According to the advisories, exploitation of these vulnerabilities would allow an authenticated attacker to execute code using a PowerShell remoting session. In order to successfully exploit this flaw, the attacker would first need to have LAN access and valid credentials for an Exchange user.
As Microsoft Exchange Server is a popular target for attackers, organizations that use Exchange Server should apply these patches as soon as possible.
Important
CVE-2023-35359, CVE-2023-35380, CVE-2023-35382, CVE-2023-35386 and CVE-2023-38154 | Windows Kernel Elevation of Privilege Vulnerability
CVE-2023-35359, CVE-2023-35380, CVE-2023-35382, CVE-2023-35386, and CVE-2023-38154 are EoP vulnerabilities in the Windows Kernel. All five vulnerabilities were assigned a CVSSv3 score of 7.8 and four are rated as “Exploitation More Likely,” with CVE-2023-38154 rated as “Exploitation Unlikely.” A local, authenticated attacker could exploit this vulnerability to obtain SYSTEM privileges. Four of the five vulnerabilities are attributed to researchers from Google Project Zero.
In 2023, including these five vulnerabilities, 33 EoP flaws were discovered in the Windows Kernel.
Important
CVE-2023-36900 | Windows Common Log File System Driver Elevation of Privilege Vulnerability
CVE-2023-36900 is an EoP vulnerability in the Windows Common Log File System (CLFS) Driver. It was assigned a CVSSv3 score of 7.8 and is rated as “Exploitation More Likely.” An authenticated attacker could exploit this vulnerability to gain SYSTEM privileges.
This is the fifth EoP vulnerability discovered in the Windows CLFS Driver in 2023, two of which were exploited in the wild as zero-days (CVE-2023-23376, CVE-2023-28252).
ADV230003 | Microsoft Office Defense in Depth Update
Microsoft released security advisory ADV230003 as part of its August Patch Tuesday release to provide “enhanced security as a defense in depth measure.” This update is in response to the discovery of CVE-2023-36884, a security feature bypass vulnerability (previously categorized as RCE by Microsoft) affecting Windows and Windows Server installations that was disclosed as part of the July 2023 Patch Tuesday release. While ADV230003 does not directly address CVE-2023-36884, it was included as part of this month’s release as it “stops the attack chain” that leads to CVE-2023-36884. Organizations are encouraged to apply the Office updates listed in the advisory and apply the latest Windows updates for August.
Microsoft also updated its advisory page for CVE-2023-36884 as part of its August Patch Tuesday, including updating the title to a “Security Feature Bypass” in Windows Search, while the CVSSv3 score was reduced to 7.5 and the severity decreased from Critical to Important. Microsoft provided patching information to address the vulnerability.
Tenable Solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains August 2023.
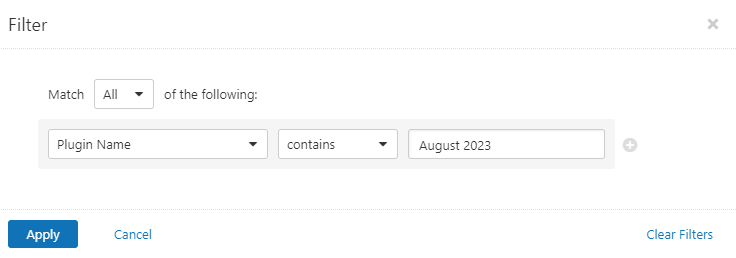
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable Vulnerability Management (formerly Tenable.io):
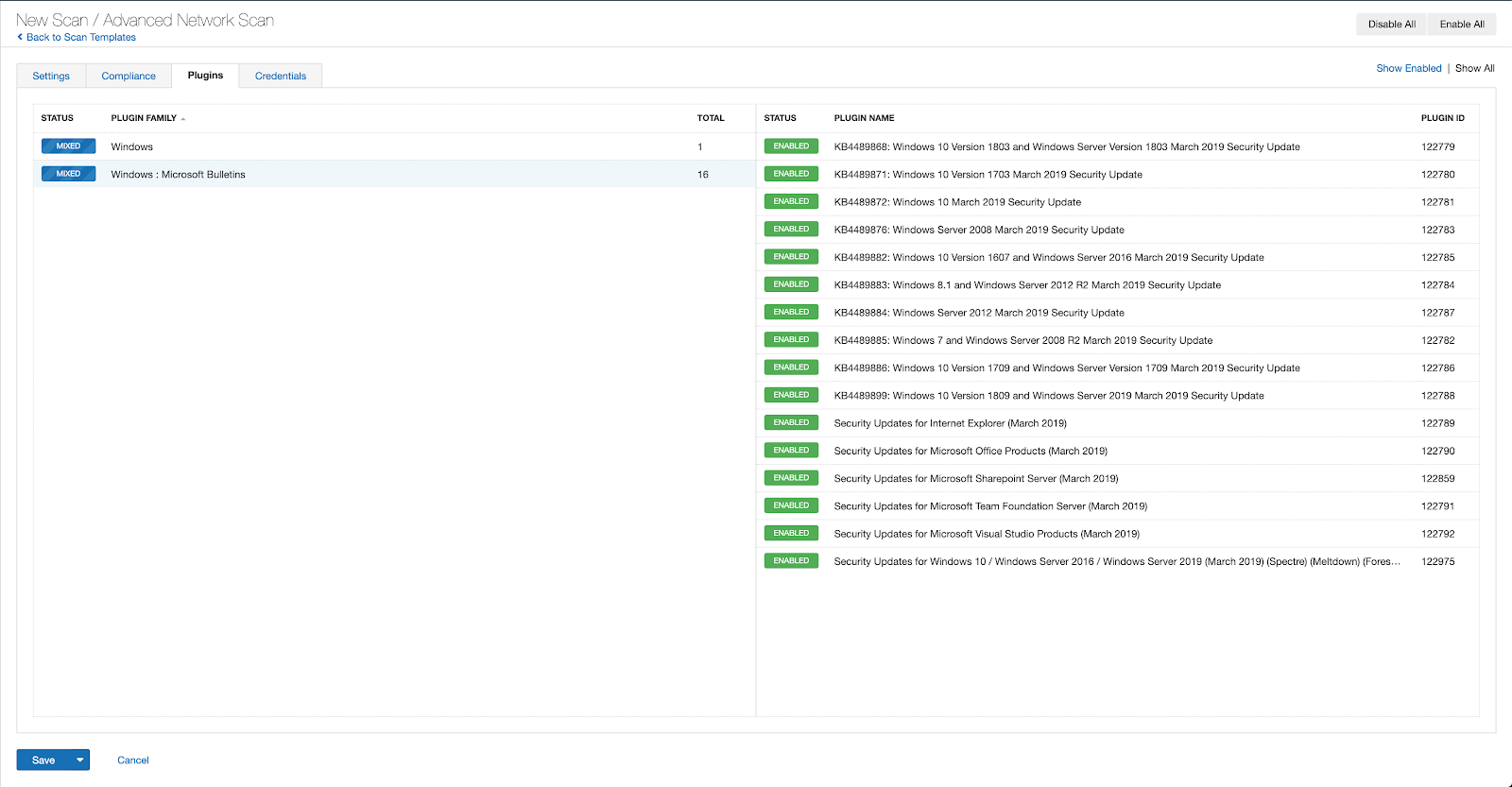
A list of all the plugins released for Tenable’s August 2023 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's August 2023 Security Updates
- Tenable plugins for Microsoft August 2023 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

Windows 11 KB5029263 cumulative update released with 27 fixes

Microsoft has released the Windows 11 22H2 KB5029263 cumulative update to fix security vulnerabilities and introduce 27 changes, improvements, and bug fixes.
KB5029263 is a mandatory Windows 11 cumulative update containing the August 2023 Patch Tuesday security updates that fix 87 vulnerabilities and two zero-days in various Microsoft products.
Windows 11 users can install today's update by going to Start > Settings > Windows Update and clicking on 'Check for Updates.'
Windows 11 KB5029263 cumulative update
Source: BleepingComputer
Windows 11 users can also manually download and install the update from the Microsoft Update Catalog.
What's new in the Windows 11 KB5029263
After installing today's KB5029263 update, Windows 11 22H2 will change its build number to 22621.2134.
Microsoft made twenty-seven changes in the Windows 11 22H2 KB5029263 update, with the highlighted ones listed below:
- Microsoft has made the brightness settings more accurate.
- Improves recognition and accuracy of Chinese characters in handwriting tools.
- If you pin a widget, it will now stay pinned.
- Microsoft fixed a bug that caused specific display and audio devices to go missing after a system resumed from sleep.
- This update fixes a bug causing VPN performance issues for those using a wireless mesh network. This was caused by excessive Address Resolution Protocol (ARP) requests to the network gateway.
Microsoft has also added additional drivers to its Windows Kernel Vulnerable Driver Blocklist to prevent Bring Your Own Vulnerable Driver (BYOVD) attacks.
The only known problem with this update is an ongoing issue causing provisioning packages not to work as expected.
You can review last month's Windows 11 KB5028254 preview update bulletin for a complete list of changes in this cumulative update.
Windows 10 KB5029244 and KB5029247 updates released

Microsoft has released Windows 10 KB5029244 and KB5028168 cumulative updates for versions 22H2, 21H2, and 1809 to fix problems and add new features to the operating system.
Microsoft will automatically install security updates released as part of the August 2023 Patch Tuesday within the next few days, as they contain important security fixes.
Windows 10 KB5029244 update
Source: BleepingComputer
You can install today's update now by going to Settings, clicking on Windows Update, and selecting 'Check for Updates.'
Here's a list of updates released today:
- Windows 10 version 1507 — KB5029259 (OS Build 10240.20107)
- Windows 10 version 1607 — KB5029242 (OS Build 14393.6167)
- Windows 10 version 1703 — EOS
- Windows 10 version 1709 — EOS
- Windows 10 version 1803 — EOS
- Windows 10 version 1809 — KB5029247 (OS Build 17763.4737)
- Windows 10 version 1903 — EOS
- Windows 10 version 1909 — EOS
- Windows 10 version 2004/21H1/20H2/21H1 — EOS/EOS
- Windows 10 version 21H2, and 22H2 — KB5029244 (OS Builds 19044.3324 and 19045.3324)
What's new in the August KB5029244 update
There are a lot of bug fixes in the KB5029244 update, including a fix for an issue that might affect your computer when you are playing a game that causes a "Timeout Detection and Recovery (TDR) error.
Another bug has been fixed that affects specific display and audio devices, which are missing after your system resumes from sleep.
Likewise, if you had VPN issues, installing today's update should help. This update addresses an issue that might cause some VPN clients not to establish a connection.
Finally, Microsoft has fixed a search interface glitch that blocked the Start menu actions and prevented users from closing the search panel.
The full list of fixes, bugs, and changes can be found in the KB5029244 support bulletin.
Microsoft August 2023 Patch Tuesday warns of 2 zero-days, 87 flaws

Today is Microsoft's August 2023 Patch Tuesday, with security updates for 87 flaws, including two actively exploited and twenty-three remote code execution vulnerabilities.
While twenty-three RCE bugs were fixed, Microsoft only rated six as 'Critical.'
The number of bugs in each vulnerability category is listed below:
- 18 Elevation of Privilege vulnerabilities
- 3 Security Feature Bypass vulnerabilities
- 23 Remote Code Execution vulnerabilities
- 10 Information Disclosure vulnerabilities
- 8 Denial of Service vulnerabilities
- 12 Spoofing vulnerabilities
These counts do not include twelve Microsoft Edge (Chromium) vulnerabilities fixed earlier this month.
Two actively exploited vulnerabilities
This month's Patch Tuesday fixes two zero-day vulnerabilities, with both exploited in attacks and one of them publicly disclosed.
Microsoft classifies a vulnerability as a zero-day if it is publicly disclosed or actively exploited with no official fix available.
The two actively exploited zero-day vulnerabilities in today's updates are:
ADV230003 - Microsoft Office Defense in Depth Update (publicly disclosed)
Microsoft has released an Office Defense in Depth update to fix a patch bypass of the previously fixed and actively exploited CVE-2023-36884 security bypass flaw.
While Microsoft initially investigated the flaw as a remote code execution flaw, it was later determined to be a security feature bypass.
This flaw allowed threat actors to create specially crafted Microsoft Office documents that could bypass the Mark of the Web (MoTW) security feature, causing files to be opened without displaying a security warning.
The vulnerability was actively exploited by the RomCom hacking group, who was previously known to deploy the Industrial Spy ransomware in attacks. The ransomware operation has since rebranded as 'Underground,' under which they continue to extort victims.
The flaw was discovered by Paul Rascagneres and Tom Lancaster with Volexity.
CVE-2023-38180 - .NET and Visual Studio Denial of Service Vulnerability
Microsoft has fixed an actively exploited vulnerability that can cause a DDoS attack on .NET applications and Visual Studio.
Unfortunately, Microsoft did not share any additional details on how this flaw was used in attacks and did not disclose who discovered the vulnerability.
Recent updates from other companies
Other vendors who released updates or advisories in August 2023 include:
- Adobe released security updates for Adobe Acrobat, Reader, Commerce, and Dimension.
- AMD released numerous security updates today for new hardware attacks and flaws.
- Cisco released security updates for Cisco Secure Web Appliance and Cisco AnyConnect.
- A new Collide+Power side-channel attack impacts almost all CPUs
- Google released the Android August 2023 updates to fix actively exploited vulnerabilities.
- A new Inception attack (CVE-2023-20569) leaks secrets from all AMD Zen CPUs.
- Ivanti fixed a remote unauthenticated API access vulnerability affecting MobileIron Core.
- Microsoft fixed a flaw in Power Platform Custom Connectors after getting some heat for taking too long.
- MOVEit released security updates that fixes a critical-severity SQL injection bug and two other less severe vulnerabilities.
- PaperCut fixed a critical vulnerability tracked as CVE-2023-39143.
- SAP has released its August 2023 Patch Day updates.
- VMware fixed numerous flaws in VMware Horizon Server.
- Zoom fixed fifteen vulnerabilities.
A joint report by the CISA, the NSA, and the FBI, Five Eyes cybersecurity authorities shared a list of the 12 most exploited vulnerabilities throughout 2022.
The August 2023 Patch Tuesday Security Updates
Below is the complete list of resolved vulnerabilities in the August 2023 Patch Tuesday updates.
To access the full description of each vulnerability and the systems it affects, you can view the full report here.
| Tag | CVE ID | CVE Title | Severity |
|---|---|---|---|
| .NET Core | CVE-2023-38178 | .NET Core and Visual Studio Denial of Service Vulnerability | Important |
| .NET Core | CVE-2023-35390 | .NET and Visual Studio Remote Code Execution Vulnerability | Important |
| .NET Framework | CVE-2023-36873 | .NET Framework Spoofing Vulnerability | Important |
| ASP .NET | CVE-2023-38180 | .NET and Visual Studio Denial of Service Vulnerability | Important |
| ASP.NET | CVE-2023-36899 | ASP.NET Elevation of Privilege Vulnerability | Important |
| ASP.NET and Visual Studio | CVE-2023-35391 | ASP.NET Core SignalR and Visual Studio Information Disclosure Vulnerability | Important |
| Azure Arc | CVE-2023-38176 | Azure Arc-Enabled Servers Elevation of Privilege Vulnerability | Important |
| Azure DevOps | CVE-2023-36869 | Azure DevOps Server Spoofing Vulnerability | Important |
| Azure HDInsights | CVE-2023-38188 | Azure Apache Hadoop Spoofing Vulnerability | Important |
| Azure HDInsights | CVE-2023-35393 | Azure Apache Hive Spoofing Vulnerability | Important |
| Azure HDInsights | CVE-2023-35394 | Azure HDInsight Jupyter Notebook Spoofing Vulnerability | Important |
| Azure HDInsights | CVE-2023-36881 | Azure Apache Ambari Spoofing Vulnerability | Important |
| Azure HDInsights | CVE-2023-36877 | Azure Apache Oozie Spoofing Vulnerability | Important |
| Dynamics Business Central Control | CVE-2023-38167 | Microsoft Dynamics Business Central Elevation Of Privilege Vulnerability | Important |
| Mariner | CVE-2023-35945 | Unknown | Unknown |
| Memory Integrity System Readiness Scan Tool | ADV230004 | Memory Integrity System Readiness Scan Tool Defense in Depth Update | Moderate |
| Microsoft Dynamics | CVE-2023-35389 | Microsoft Dynamics 365 On-Premises Remote Code Execution Vulnerability | Important |
| Microsoft Edge (Chromium-based) | CVE-2023-38157 | Microsoft Edge (Chromium-based) Security Feature Bypass Vulnerability | Moderate |
| Microsoft Edge (Chromium-based) | CVE-2023-4068 | Chromium: CVE-2023-4068 Type Confusion in V8 | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4072 | Chromium: CVE-2023-4072 Out of bounds read and write in WebGL | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4071 | Chromium: CVE-2023-4071 Heap buffer overflow in Visuals | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4073 | Chromium: CVE-2023-4073 Out of bounds memory access in ANGLE | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4075 | Chromium: CVE-2023-4075 Use after free in Cast | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4074 | Chromium: CVE-2023-4074 Use after free in Blink Task Scheduling | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4076 | Chromium: CVE-2023-4076 Use after free in WebRTC | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4077 | Chromium: CVE-2023-4077 Insufficient data validation in Extensions | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4078 | Chromium: CVE-2023-4078 Inappropriate implementation in Extensions | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4070 | Chromium: CVE-2023-4070 Type Confusion in V8 | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-4069 | Chromium: CVE-2023-4069 Type Confusion in V8 | Unknown |
| Microsoft Exchange Server | CVE-2023-38185 | Microsoft Exchange Server Remote Code Execution Vulnerability | Important |
| Microsoft Exchange Server | CVE-2023-35388 | Microsoft Exchange Server Remote Code Execution Vulnerability | Important |
| Microsoft Exchange Server | CVE-2023-35368 | Microsoft Exchange Remote Code Execution Vulnerability | Important |
| Microsoft Exchange Server | CVE-2023-38181 | Microsoft Exchange Server Spoofing Vulnerability | Important |
| Microsoft Exchange Server | CVE-2023-38182 | Microsoft Exchange Server Remote Code Execution Vulnerability | Important |
| Microsoft Exchange Server | CVE-2023-21709 | Microsoft Exchange Server Elevation of Privilege Vulnerability | Important |
| Microsoft Office | ADV230003 | Microsoft Office Defense in Depth Update | Moderate |
| Microsoft Office | CVE-2023-36897 | Visual Studio Tools for Office Runtime Spoofing Vulnerability | Important |
| Microsoft Office Excel | CVE-2023-36896 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2023-35371 | Microsoft Office Remote Code Execution Vulnerability | Important |
| Microsoft Office Outlook | CVE-2023-36893 | Microsoft Outlook Spoofing Vulnerability | Important |
| Microsoft Office Outlook | CVE-2023-36895 | Microsoft Outlook Remote Code Execution Vulnerability | Critical |
| Microsoft Office SharePoint | CVE-2023-36891 | Microsoft SharePoint Server Spoofing Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2023-36894 | Microsoft SharePoint Server Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2023-36890 | Microsoft SharePoint Server Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2023-36892 | Microsoft SharePoint Server Spoofing Vulnerability | Important |
| Microsoft Office Visio | CVE-2023-35372 | Microsoft Office Visio Remote Code Execution Vulnerability | Important |
| Microsoft Office Visio | CVE-2023-36865 | Microsoft Office Visio Remote Code Execution Vulnerability | Important |
| Microsoft Office Visio | CVE-2023-36866 | Microsoft Office Visio Remote Code Execution Vulnerability | Important |
| Microsoft Teams | CVE-2023-29328 | Microsoft Teams Remote Code Execution Vulnerability | Critical |
| Microsoft Teams | CVE-2023-29330 | Microsoft Teams Remote Code Execution Vulnerability | Critical |
| Microsoft WDAC OLE DB provider for SQL | CVE-2023-36882 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | Important |
| Microsoft Windows | CVE-2023-20569 | AMD: CVE-2023-20569 Return Address Predictor | Important |
| Microsoft Windows Codecs Library | CVE-2023-38170 | HEVC Video Extensions Remote Code Execution Vulnerability | Important |
| Reliability Analysis Metrics Calculation Engine | CVE-2023-36876 | Reliability Analysis Metrics Calculation (RacTask) Elevation of Privilege Vulnerability | Important |
| Role: Windows Hyper-V | CVE-2023-36908 | Windows Hyper-V Information Disclosure Vulnerability | Important |
| SQL Server | CVE-2023-38169 | Microsoft OLE DB Remote Code Execution Vulnerability | Important |
| Tablet Windows User Interface | CVE-2023-36898 | Tablet Windows User Interface Application Core Remote Code Execution Vulnerability | Important |
| Windows Bluetooth A2DP driver | CVE-2023-35387 | Windows Bluetooth A2DP driver Elevation of Privilege Vulnerability | Important |
| Windows Cloud Files Mini Filter Driver | CVE-2023-36904 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | Important |
| Windows Common Log File System Driver | CVE-2023-36900 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Important |
| Windows Cryptographic Services | CVE-2023-36907 | Windows Cryptographic Services Information Disclosure Vulnerability | Important |
| Windows Cryptographic Services | CVE-2023-36906 | Windows Cryptographic Services Information Disclosure Vulnerability | Important |
| Windows Defender | CVE-2023-38175 | Microsoft Windows Defender Elevation of Privilege Vulnerability | Important |
| Windows Fax and Scan Service | CVE-2023-35381 | Windows Fax Service Remote Code Execution Vulnerability | Important |
| Windows Group Policy | CVE-2023-36889 | Windows Group Policy Security Feature Bypass Vulnerability | Important |
| Windows HTML Platform | CVE-2023-35384 | Windows HTML Platforms Security Feature Bypass Vulnerability | Important |
| Windows Kernel | CVE-2023-35359 | Windows Kernel Elevation of Privilege Vulnerability | Important |
| Windows Kernel | CVE-2023-38154 | Windows Kernel Elevation of Privilege Vulnerability | Important |
| Windows Kernel | CVE-2023-35382 | Windows Kernel Elevation of Privilege Vulnerability | Important |
| Windows Kernel | CVE-2023-35386 | Windows Kernel Elevation of Privilege Vulnerability | Important |
| Windows Kernel | CVE-2023-35380 | Windows Kernel Elevation of Privilege Vulnerability | Important |
| Windows LDAP - Lightweight Directory Access Protocol | CVE-2023-38184 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | Important |
| Windows Message Queuing | CVE-2023-36909 | Microsoft Message Queuing Denial of Service Vulnerability | Important |
| Windows Message Queuing | CVE-2023-35376 | Microsoft Message Queuing Denial of Service Vulnerability | Important |
| Windows Message Queuing | CVE-2023-38172 | Microsoft Message Queuing Denial of Service Vulnerability | Important |
| Windows Message Queuing | CVE-2023-35385 | Microsoft Message Queuing Remote Code Execution Vulnerability | Critical |
| Windows Message Queuing | CVE-2023-35383 | Microsoft Message Queuing Information Disclosure Vulnerability | Important |
| Windows Message Queuing | CVE-2023-36913 | Microsoft Message Queuing Information Disclosure Vulnerability | Important |
| Windows Message Queuing | CVE-2023-35377 | Microsoft Message Queuing Denial of Service Vulnerability | Important |
| Windows Message Queuing | CVE-2023-38254 | Microsoft Message Queuing Denial of Service Vulnerability | Important |
| Windows Message Queuing | CVE-2023-36911 | Microsoft Message Queuing Remote Code Execution Vulnerability | Critical |
| Windows Message Queuing | CVE-2023-36910 | Microsoft Message Queuing Remote Code Execution Vulnerability | Critical |
| Windows Message Queuing | CVE-2023-36912 | Microsoft Message Queuing Denial of Service Vulnerability | Important |
| Windows Mobile Device Management | CVE-2023-38186 | Windows Mobile Device Management Elevation of Privilege Vulnerability | Important |
| Windows Projected File System | CVE-2023-35378 | Windows Projected File System Elevation of Privilege Vulnerability | Important |
| Windows Reliability Analysis Metrics Calculation Engine | CVE-2023-35379 | Reliability Analysis Metrics Calculation Engine (RACEng) Elevation of Privilege Vulnerability | Important |
| Windows Smart Card | CVE-2023-36914 | Windows Smart Card Resource Management Server Security Feature Bypass Vulnerability | Important |
| Windows System Assessment Tool | CVE-2023-36903 | Windows System Assessment Tool Elevation of Privilege Vulnerability | Important |
| Windows Wireless Wide Area Network Service | CVE-2023-36905 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability | Important |
Patch Tuesday: Adobe Patches 30 Acrobat, Reader Vulns
Adobe rolls out a big batch of security updates to fix at least 30 Acrobat and Reader vulnerabilities affecting Windows and macOS users.
The post Patch Tuesday: Adobe Patches 30 Acrobat, Reader Vulns appeared first on SecurityWeek.
Meet the Brains Behind the Malware-Friendly AI Chat Service ‘WormGPT’
WormGPT, a private new chatbot service advertised as a way to use Artificial Intelligence (AI) to help write malicious software without all the pesky prohibitions on such activity enforced by ChatGPT and Google Bard, has started adding restrictions on how the service can be used. Faced with customers trying to use WormGPT to create ransomware and phishing scams, the 23-year-old Portuguese programmer who created the project now says his service is slowly morphing into “a more controlled environment.” The large language models (LLMs) made by ChatGPT parent OpenAI or Google or Microsoft all have various safety measures designed to prevent people from abusing them for nefarious purposes — such as creating malware or hate speech. In contrast, WormGPT has promoted itself as a new LLM that was created specifically for cybercrime activities.
New Downfall attacks on Intel CPUs steal encryption keys, data

A senior research scientist at Google has devised new CPU attacks to exploit a vulnerability dubbed Downfall that affects multiple Intel microprocessor families and allows stealing passwords, encryption keys, and private data like emails, messages, or banking info from users that share the same computer.
Tracked as CVE-2022-40982, the flaw is a transient execution side-channel issue and impacts all processors based on Intel microarchitectures Skylake through Ice Lake.
A threat actor exploiting the security issue can extract sensitive information that is protected by Software Guard eXtensions (SGX), Intel’s hardware-based memory encryption that separates in memory code and data from software on the system.
SGX is currently supported only on server central processing units and offers a trusted isolated environment for software that not even the operating system can access.
gather secret data
Daniel Moghimi, the Google researcher who discovered the vulnerability and reported it responsibly to Intel, says that his Downfall attack techniques take advantage of the gather instruction that “leaks the content of the internal vector register file during speculative execution.”
Gather is part of memory optimizations in Intel processors, used to speed up accessing scattered data in memory. However, as Moghimi explains in a technical paper published today:
“The gather instruction appears to use a temporal buffer shared across sibling CPU threads, and it transiently forwards data to later dependent instructions, and the data belongs to a different process and gather execution running on the same core.”
Moghimi developed two Downfall attack techniques, Gather Data Sampling (GDS) - which is also the name Intel uses to refer to the issue and Gather Value Injection (GVI) - which combines GDS with the Load Value Injection (LVI) technique disclosed in 2020.
Using the GDS technique, Moghimi was able to steal AES 128-bit and 256-bit cryptographic keys on a separate virtual machine (VM) from the controlled one, with each system on sibling threads of the same CPU core.
In less than 10 seconds, eight bytes at a time, the researcher managed to steal AES round keys and combine them to break the encryption.
“For 100 different keys, the first run of the attack was 100% successful for AES-128. The first run of the attack was 86% successful for AES-256.”
The researcher notes that failed attempts mean that recovering the entire key required running the attack multiple times because data for the master key did not appear with a high frequency within 10 seconds.
Apart from encryption keys, Moghimi provides variants of the GDS attack that can steal arbitrary data at rest because of two conditions where the CPU prefetches this type of information into the SIMD register buffers.
Threat assessment and microcode performance impact
Dawnfall attacks require an attacker to be on the same physical processor core as the victim, a context that is provided by today’s shared computing model, Moghimi notes.
However, a local program, such as malware, could potentially exploit the flaw to steal sensitive information.
Intel learned about the Downfall/GDS vulnerability last August and collaborated with Moghimi on the findings. A microcode update is now available to mitigate the issue.
Details about the vulnerability stayed private for almost a year to give time to original equipment manufacturers (OEMs) and communication service providers (CSPs) to test and validate the solution, as well as prepare the necessary updates for their customers.
Intel told BleepingComputer that the issue does not impact Alder Lake, Raptor Lake, and Sapphire Rapids and that Downfall affects the following three families of processors:
- Skylake family (Skylake, Cascade Lake, Cooper Lake, Amber Lake, Kaby Lake, Coffee Lake, Whiskey Lake, Comet Lake)
- Tiger Lake family
- Ice Lake family (Ice Lake, Rocket Lake)
Vivek Tiwari, Intel's Vice President of Remediation and Response Engineering, believes that “trying to exploit this outside of a controlled lab environment would be a complex undertaking.”
In a statement for BleepingComputer, Intel said that customers can review the risk assessment guidance from the company and decide on disabling the microcode mitigation through mechanisms available in Windows and Linux as well as virtual machine managers (VMMs).
Such a decision may be driven by concerns about potential performance issues from the Downfall/GDS mitigation or because the issue does not represent a threat to the environment.
Intel provides customers with both threat assessment and performance analysis information, which concludes that the impact of the issue in certain environments may be minimal.
A potential impact exists in conditions where gather instructions are frequently executed, which is specific to high-performance computing (HPC) environments.
However, the chipmaker says the issue may not be considered a threat in an HPC context because of the conditions of the attack and the typical configuration of these environments.
“For example, an attacker would need to be running on the same physical core as the target and be able to run untrusted code, among other things, which are not typical in these environments” - Intel
Software-based mitigations
Eliminating the risk of Downfall/GDS attacks requires a hardware redesign, which comes at a cost that the industry is not yet ready to pay.
Software-based alternatives exist, although these come with caveats and are temporary solutions to the problem. Moghimi proposes four such alternatives, three of them with significant disadvantages:
- Disabling simultaneous multithreading (SMT) can partially mitigate GDS and GVI attacks, but cutting hyperthreading comes with a 30% loss in performance and leaks across context switching still occur
- Disallowing affected instructions through the operating system and the compiler to prevent them from leaking secrets to gather; the downside is some apps could be disrupted and the leak still happens if some instructions are missed
- Disabling gather. The drawback here is that applications using the instruction could become slow or even break
- Preventing transient data forwarding after the gather instruction (adding a load fence, e.g. the lfence instruction) can mitigate Downfall and is the solution that Intel adopted with the latest microcode update
Moghimi warns, though, that without eliminating the root cause of the problem “automated testing can practically find new vulnerabilities in CPUs.”
Such tools are not easy to create because they need to better cover the hardware and the supported instructions, a challenging task given the hardware complexity and the proprietary barriers.
Daniel Moghimi is scheduled to talk about the Downfall vulnerability and attack techniques at the Black Hat USA security conference tomorrow.
Interpol takes down 16shop phishing-as-a-service platform

A joint operation between Interpol and cybersecurity firms has led to an arrest and shutdown of the notorious 16shop phishing-as-a-service (PhaaS) platform.
Phishing-as-a-service platforms offer cybercriminals a one-stop-shop to conduct phishing attacks. These platforms typically include everything you need, including email distribution, ready-made phishing kits for well-known brands, hosting, data proxying, victim overview dashboards, and other tools that help increase the success of their operations.
These platforms are a significant risk as they lower the bar of entry for inexperienced cybercriminals, offering them a simple and cost-effective way to launch phishing attacks with only a few clicks.
Group-IB, which aided Interpol in the takedown operation, reports that the 16shop platform offered phishing kits that targeted Apple, PayPal, American Express, Amazon, and Cash App accounts, among others.
Group-IB's telemetry data shows that 16shop is responsible for creating 150,000 phishing pages, which targeted people mainly from Germany, Japan, France, the USA, and the UK.
Interpol's announcement mentions that at least 70,000 users from 43 countries were compromised by phishing pages created through 16shop.
The data stolen in these attacks include personal details, account emails and passwords, ID cards, credit card numbers, and telephone numbers.
Arrest of operator
Interpol's operation resulted in the arrest of the 21-year-old platform operator in February 2022 in Indonesia and later led to the apprehension of two facilitators, one in Japan and one in Indonesia.
"A notorious 'phishing-as-a-service' (PaaS) platform known as '16shop' has been shut down in a global investigation coordinated by INTERPOL, with Indonesian authorities arresting its operator and one of its facilitators, with another arrested in Japan," reads Interpol's press release.
"Assisted with information from an array of private sector partners, the INTERPOL team was soon able to determine the identity and probable location of the platform's administrator," Interpol further added.
A US-based company hosted 16shop's servers, but its registration information showed that it was based in Indonesia.
The police in Indonesia arrested the young man and seized electronic items and several luxury vehicles that were in the operator's possession.
The two facilitators were identified and subsequently arrested following the apprehension of the admin, suggesting he may have divulged information about his accomplices.
Warning: TorrentFreak’s Twitter / X Account Has Been Hijacked
Earlier today someone managed to hijack our Twitter / X account. The original @torrentfreak handle was deleted and the new account now appears as @ethereumfdn with all of our followers still attached. Obviously it can't be trusted.
From: TF, for the latest news on copyright battles, piracy and more.
White House Holds First-Ever Summit on the Ransomware Crisis Plaguing the Nation’s Public Schools
CISA will step up training for the K-12 sector and technology providers, including Amazon Web Services and Cloudflare, will offer grants and free software.
The post White House Holds First-Ever Summit on the Ransomware Crisis Plaguing the Nation’s Public Schools appeared first on SecurityWeek.
UK Electoral Commission discloses a data breach
The UK Electoral Commission suffered a data breach that exposed voters’ personal information between 2014 and 2022. The UK Electoral Commission disclosed a data breach that exposed the personal information of voters in the United Kingdom between 2014 and 2022. The Commission notified the Information Commissioner’s Office. “Today we announced that we have been the […]
The post UK Electoral Commission discloses a data breach appeared first on Security Affairs.
Android 14 to block connections to unencrypted cellular networks

Image: Midjourney
Google has announced new cellular security features for its upcoming Android 14, expected later this month, that aim to protect business data and communications.
Android 14 will allow consumers and enterprises to turn off support for 2G on their devices or a managed device fleet and disable support for null-cipher (unencrypted) cellular connectivity at the modem level.
"Android is the first mobile operating system to introduce advanced cellular security mitigations for both consumers and enterprises," reads Google's announcement
"Android 14 introduces support for IT administrators to disable 2G support in their managed device fleet [and] also introduces a feature that disables support for null-ciphered cellular connectivity."
Enterprise Stingray protection
Google's announcement highlights the risks of false base stations and "Stingray" attacks that can intercept users' data, voice, and SMS by eavesdropping on network traffic.
Stingrays are cell-site simulators that mimic cell towers to trick in-range devices to connect to them. This allows for intercepting sensitive personal data such as call metadata, SMS and voice call content, data usage and browsing history, and device IMSI.
Stingray attacks have been largely mitigated in 4G. However, since downgrading connections to 2G remains possible, rogue cell stations can still perform these powerful man-in-the-middle attacks.
Google first offered the option to turn off 2G connectivity on Android 12 by going through 'Settings → Network & Internet → SIMs → Allow 2G'.
In Android 13, that option is to be found on 'Settings → Network & Internet → SIMs → [select SIM] → Allow 2G.'
2G connectivity toggle in Android 13
Source: BleepingComputer
Starting in Android 14, those managing device fleets, such as government agencies, enterprise entities, or other organizations, can restrict 2G connectivity downgrades on all devices under their control.
This option is added on top of over 200 controls available in Android Enterprise, including the ability to disable WiFi, Bluetooth, and data signaling over USB.
Stingray attacks have become more common over the past couple of years, with law enforcement and surveillance firms utilizing them to spy on cell phones, so this feature comes as a welcome addition to enterprise security.
Blocking unencrypted networks
While all IP-based user traffic on Android is end-to-end encrypted, ensuring that any interceptions won't result in data breaches, Google warns that certain communication types, such as circuit-switched voice calls and SMS messages, can still be exposed on cellular networks.
The exposed data is typically protected by the cellular link layer cipher, which the users have no control or visibility over, so its strength and reliability are doubtful.
Moreover, recent reports have shown that null ciphers (no encryption) are not uncommon in commercial networks, exposing the mentioned data in cleartext and easily readable form to those who can intercept it.
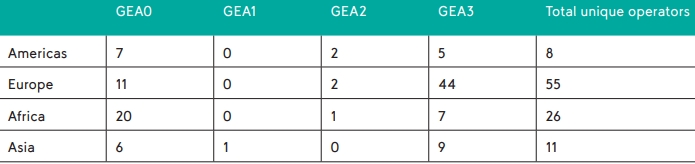
Network operators using null-cipher (GEA0)
Source: umlaut.com
To mitigate this risk, Android 14 introduces a feature that allows users to turn off support for null-cipher connections at the modem level for devices that adopt the latest radio hardware abstraction layer (HAL).
Like in the 2G disabling feature, emergency calls can still downgrade to null-cipher connections to avoid jeopardizing users' safety.
New Inception attack leaks sensitive data from all AMD Zen CPUs

Researchers have discovered a new and powerful transient execution attack called 'Inception' that can leak privileged secrets and data using unprivileged processes on all AMD Zen CPUs, including the latest models.
Transient execution attacks exploit a feature present on all modern processors named speculative execution, which dramatically increases the performance of CPUs by guessing what will be executed next before a slower operation if completed.
If the guess is correct, the CPU has increased performance by not waiting for an operation to finish, and if it guessed wrong, it simply rolls back the change and continues the operation using the new outcome.
The problem with speculative execution is that it can leave traces that attackers can observe or analyze to retrieve valuable data that should be otherwise protected.
Researchers at ETH Zurich have now combined an older technique named 'Phantom speculation' (CVE-2022-23825) with a new transient execution attack called 'Training in Transient Execution' (TTE) to create an even more powerful 'Inception' attack.
Phantom speculation allows attackers to trigger mispredictions without needing any branch at the misprediction source, i.e., create a speculative execution period ("transient window") at arbitrary XOR instructions.
TTE is the manipulation of future mispredictions by injecting new predictions into the branch predictor to create exploitable speculative executions.
The Inception attack, tracked as CVE-2023-20569, is a novel attack that combines the concepts described above, allowing an attacker to make the CPU believe that an XOR instruction (simple binary operation) is a recursive call instruction.
This causes it to overflow the return stack buffer with a target address controlled by the attacker, allowing them to leak arbitrary data from unprivileged processes running on any AMD Zen CPU.
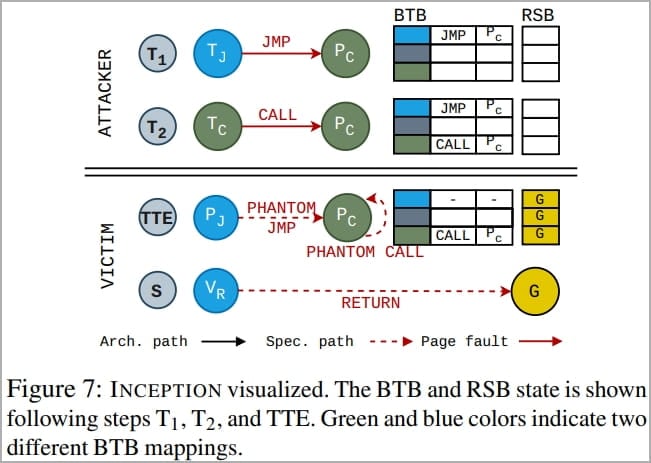
Inception logic diagram (ETH Zurich)
The leak is possible even if all mitigations to known speculative execution attacks like Spectre or transient control-flow hijacks, such as Automatic IBRS, have already been applied.
Also, the data leak rate achieved through Inception is 39 bytes/sec, which would take about half a second to steal a 16-character password and 6.5 seconds for an RSA key.
ETH Zurich's team published separate technical papers for Inception and Phantom for those who want to dive deeper into the specifics of the attacks.
<iframe allowfullscreen="allowfullscreen" class="embed-responsive-item" frameborder="0" mozallowfullscreen="mozallowfullscreen" msallowfullscreen="msallowfullscreen" oallowfullscreen="oallowfullscreen" scrolling="no" src="//www.youtube.com/embed/2wCjU8iJ9G4" webkitallowfullscreen="webkitallowfullscreen">
Preventing Inception attacks
The researchers say that all AMD Zen-based Ryzen and EPYC CPUs, from Zen 1 to Zen 4, are vulnerable to Phantom and Inception.
Specific TTE variants potentially impact Intel CPUs, but Phantom is hard to exploit on Intel thanks to eIBRS mitigations.
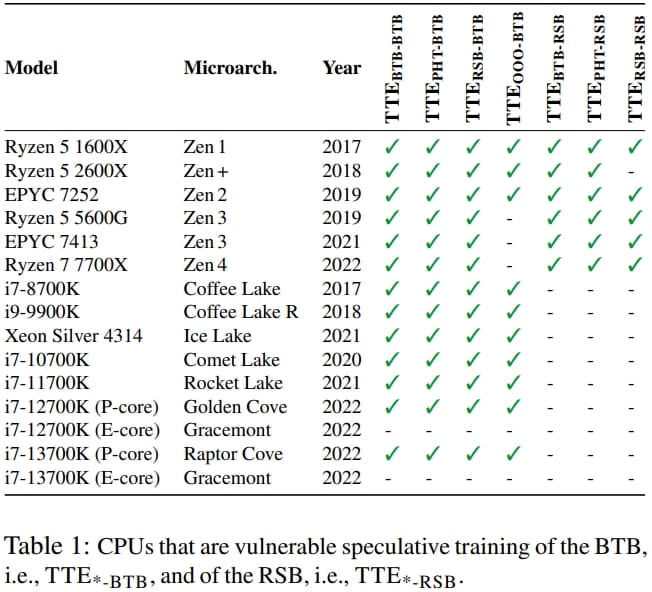
Impact of specific TTE variants on modern CPU models (ETH Zurich)
Although the proof-of-concept created by the ETH Zurich team is meant to be executed on Linux, the attacks should work on any operating system using vulnerable AMD CPUs, as this is a hardware flaw, not a software one.
A strategy to mitigate the problem would be to fully flush the branch predictor state when switching between distrusting contexts; however, this introduces a performance overhead between 93.1% and 216.9% on older Zen 1(+) and Zen 2 CPUs.
For Zen 3 and Zen 4 CPUs, adequate hardware support for this mitigation strategy was initially absent, but AMD has since released microcode updates to enable this feature.
Owners of Zen-based AMD processors are recommended to install the latest microcode updates, which can also arrive as part of computer vendor and/or operating system security updates.
A fix for the Phantom flaw, CVE-2022-23825, was released in the Windows July 2022 update.
BleepingComputer has contacted AMD to learn more about microcode release schedules for the impacted chip architectures, but we have yet to hear back by publication time.
Schneider Electric IGSS
1. EXECUTIVE SUMMARY
- CVSS v3 7.8
- ATTENTION: low attack complexity
- Vendor: Schneider Electric
- Equipment: IGSS (Interactive Graphical SCADA System)
- Vulnerability: Deserialization of Untrusted Data
2. RISK EVALUATION
Successful exploitation of this vulnerability may allow arbitrary code execution or loss of control of the SCADA system.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Schneider Electric reports this vulnerability affects the following IGSS (Interactive Graphical SCADA System) products:
- IGSS Dashboard (DashBoard.exe): v16.0.0.23130 and prior
3.2 VULNERABILITY OVERVIEW
3.2.1 DESERIALIZATION OF UNTRUSTED DATA CWE-502
A deserialization of untrusted data vulnerability exists in the Dashboard module that could cause an interpretation of malicious payload data, potentially leading to arbitrary code execution when an attacker gets the user to open a malicious file.
CVE-2023-3001 has been assigned to this vulnerability. A CVSS v3 base score of 7.8 has been calculated; the CVSS vector string is (AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Commercial Facilities, Critical Manufacturing, Energy
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: France
3.4 RESEARCHER
Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) working with Trend Micro Zero Day Initiative reported this vulnerability to Schneider Electric and CISA.
4. MITIGATIONS
Schneider Electric has provided version 16.0.0.23131 of Dashboard to address these vulnerabilities. The update is available for download through IGSS Master > Update IGSS Software or from the Schneider Electric support page.
If users choose not to apply the remediation provided above, they should immediately apply the following mitigations to reduce the risk of exploit:
- Review and implement the security guideline for IGSS on securing an IGSS SCADA installation.
- Follow the general security recommendation below and verify that devices are isolated on a private network and that firewalls are configured with strict boundaries for devices that require remote access.
For more information, see the Schneider Electric security notification SEVD-2023-164-02.
Schneider Electric recommends the following industry cybersecurity best practices.
- Locate control and safety system networks and remote devices behind firewalls and isolate them from the business network.
- Install physical controls so no unauthorized personnel can access your industrial control and safety systems, components, peripheral equipment, and networks.
- Place all controllers in locked cabinets and never leave them in the “Program” mode.
- Never connect programming software to any network other than the network intended for that device.
- Scan all methods of mobile data exchange with the isolated network such as CDs, USB drives, etc. before use in the terminals or any node connected to these networks.
- Never allow mobile devices that have connected to any other network besides the intended network to connect to the safety or control networks without proper sanitation.
- Minimize network exposure for all control system devices and systems and ensure that they are not accessible from the internet.
- When remote access is required, use secure methods, such as virtual private networks (VPNs). Recognize that VPNs may have vulnerabilities and should be updated to the most current version available. Also, understand that VPNs are only as secure as the connected devices.
CISA recommends users take defensive measures to minimize the risk of exploitation of this vulnerability. CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage at cisa.gov/ics. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov/ics in the technical information paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
No known public exploits specifically target this vulnerability. This vulnerability is not exploitable remotely. This vulnerability has low attack complexity.
CISA Releases Two Industrial Control Systems Advisories
CISA released two Industrial Control Systems (ICS) advisories on August 8, 2023. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS.
- ICSA-23-220-01 Schneider Electric IGSS
- ICSA-23-220-02 Hitachi Energy RTU500 series
CISA encourages users and administrators to review the newly released ICS advisories for technical details and mitigations.
Hitachi Energy RTU500 series
1. EXECUTIVE SUMMARY
- CVSS v3 7.5
- ATTENTION: Exploitable remotely/low attack complexity
- Vendor: Hitachi Energy
- Equipment: RTU500 series
- Vulnerabilities: Stack-based Buffer Overflow
2. RISK EVALUATION
Successful exploitation of these vulnerabilities could cause a buffer overflow and reboot of the product.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Hitachi Energy reports these vulnerabilities affect the following RTU500 series products:
- RTU500 series CMU: Firmware versions 13.3.1–13.3.2
3.2 VULNERABILITY OVERVIEW
3.2.1 STACK-BASED BUFFER OVERFLOW CWE-121
A vulnerability exists in the HCI IEC 60870-5-104 function included in certain versions of the RTU500 series product. The vulnerability can only be exploited if the HCI 60870-5-104 is configured with IEC 62351-5 support and the CMU contains the license feature ‘Advanced security’ which must be ordered separately. If these preconditions are fulfilled, an attacker could exploit the vulnerability by sending a specially crafted message to the RTU500, causing the targeted RTU500 CMU to reboot. The vulnerability is caused by a missing input data validation, which eventually, if exploited, could cause an internal buffer to overflow in the HCI IEC 60870-5-104 function.
CVE-2022-2502 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.2 STACK-BASED BUFFER OVERFLOW CWE-121
A vulnerability exists in HCI IEC 60870-5-104 function included in certain versions of the RTU500 series product. The vulnerability can only be exploited if the HCI 60870-5-104 is configured with support for IEC 62351-3. After session resumption interval is expired, an RTU500 initiated update of session parameters could cause an unexpected restart due to a stack overflow.
CVE-2022-4608 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Energy
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Switzerland
3.4 RESEARCHER
Hitachi Energy reported these vulnerabilities to CISA.
4. MITIGATIONS
Hitachi Energy recommends users update to CMU Firmware versions 13.3.3 or 13.4.1.
The reported vulnerabilities affect only the RTU500 series with HCI IEC 60870-5-104 and IEC62351-5 or IEC 62351-5 configured and enabled. A possible mitigation is to disable the HCI IEC 60870-5-104 function or its IEC 62351-3 and IEC 62351-5 features if they are not used. By default, the HCI IEC 60870-5-104 and its IEC 62351-3 or IEC 62351-5 support are disabled.
Hitachi Energy recommends the following general mitigations:
- Recommended security practices and firewall configurations can help protect a process control network from attacks originating from outside the network.
- Physically protect process control systems from direct access by unauthorized personnel.
- Ensure process control systems have no direct connections to the internet and are separated from other networks via a firewall system with minimal exposed ports.
- Do not use process control systems for internet surfing, instant messaging, or receiving emails.
- Scan portable computers and removable storage media for malware prior connection to a control system.
- Enforce proper password policies and processes.
For more information, see Hitachi Energy’s Security Advisory: 8DBD000121.
CISA recommends users take defensive measures to minimize the risk of exploitation of these vulnerabilities. CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage at cisa.gov/ics. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov/ics in the technical information paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
No known public exploits specifically target these vulnerabilities. These vulnerabilities are exploitable remotely. These vulnerabilities have low attack complexity.