The Discord.io custom invite service has temporarily shut down after suffering a data breach exposing the information of 760,000 members.
Discord.io is not an official Discord site but a third-party service allowing server owners to create custom invites to their channels. Most of the community was built around the service's Discord server, with over 14,000 members.
Yesterday, a person known as 'Akhirah' began offering the Discord.io database for sale on the new Breached hacking forums. As proof of the theft, the threat actor shared four user records from the database.
For those unfamiliar with the new Breached, it is the rebirth of a popular cybercrime forum known for the sale and leaking of data stolen in data breaches.
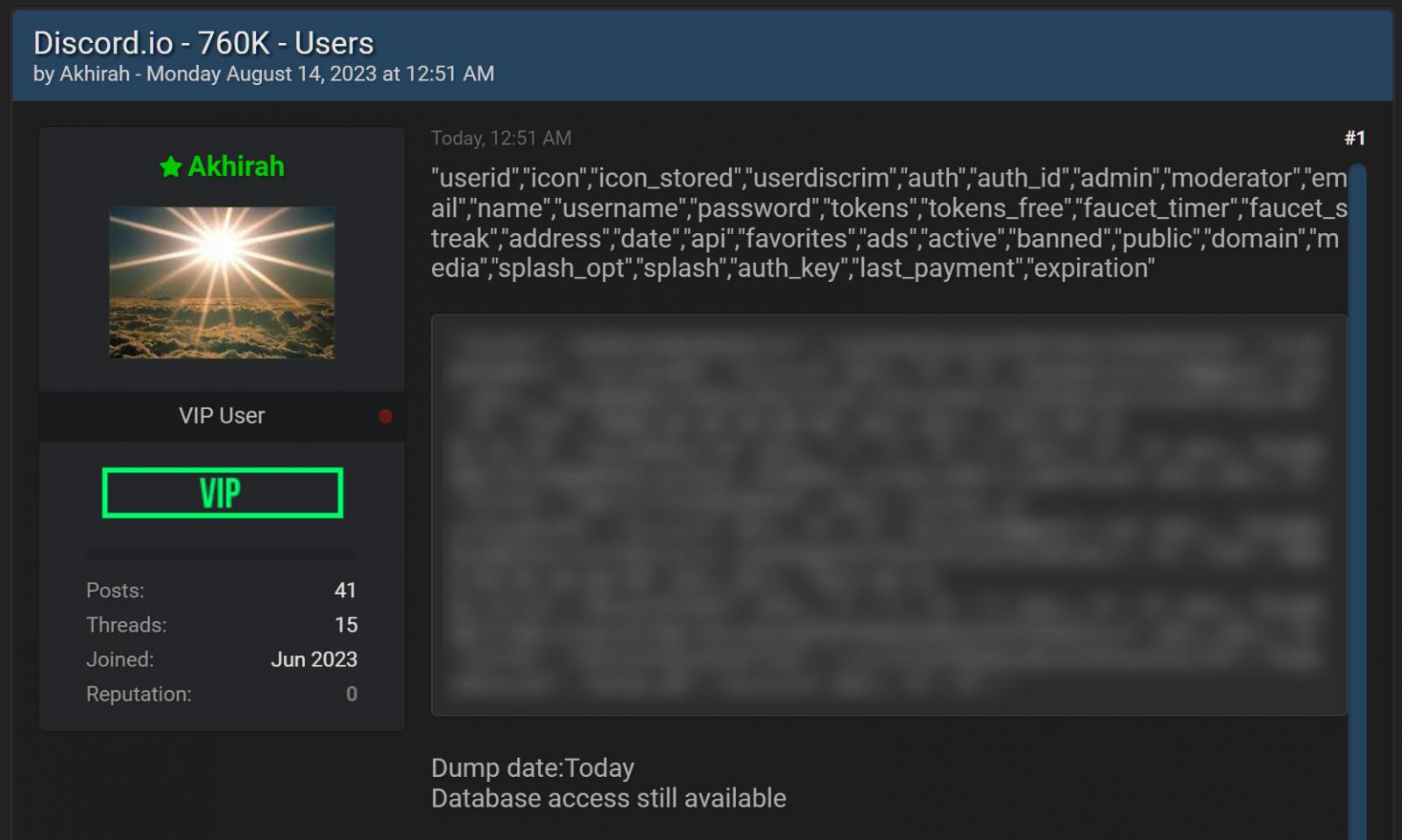
Forum post selling Discord.io database
Source: BleepingComputer
According to the threat actor, the database contains the information for 760,000 Discord.io users and includes the following types of information:
"userid","icon","icon_stored","userdiscrim","auth","auth_id","admin","moderator","email","name","username","password","tokens","tokens_free","faucet_timer","faucet_streak","address","date","api","favorites","ads","active","banned","public","domain","media","splash_opt","splash","auth_key","last_payment","expiration"
The most sensitive information in the breach is a member's username, email address, billing address (small number of people), salted and hashed password (small number of people), and Discord ID.
"This information is not private and can be obtained by anyone sharing a server with you. Its inclusion in the breach does, however, mean that other people might be able to link your Discord account to a given email address," Discord.io explained about the leaking of Discord IDs.
As first reported by StackDiary, Discord.io has confirmed the authenticity of the breach in a notice to its Discord server and website and has begun temporarily shutting down its services in response.
"Discord.io has suffered a data breach. We are stopping all operations for the foreseeable future," reads a message on the service's Discord server.
"For more information, please refer to our #breah-notification channel. We'll be updating our website soon with a copy of this message."
The website for Discord.io contains a timeline explaing that they first learned of the data breach after seeing the post on the hacking forum.
Soon after, they confirmed the authenticity of the leaked data and began shutting down its services and cancelling all paid memberships.
Discord.io says they have been contacted by the individual behind the breach and have not shared any information on how they were breached.
What should Discord.io members do?
The passwords in this breach are hashed using bcrypt, making them hardware-intensive and slow to crack.
However, email addresses can be valuable to other threat actors as they could be used for targeted phishing attacks to steal more sensitive information.
Therefore, if you are a member of Discord.io, you should be on the lookout for unusual emails with links to pages asking you to enter your password or other information.
For any updates about the breach, you should check the main website, which should contain any information about potential password resets or emails from the service.