Massive 400,000 proxy botnet built with stealthy malware infections
Researchers have uncovered a massive campaign that delivered proxy server apps to at least 400,000 Windows systems. The devices act as residential exit nodes without users' consent and a company is charging for the proxy traffic running through the machines..
Residential proxies are valuable to cybercriminals because they can help with deploying large-scale credential stuffing attacks from fresh IP addresses. They also have legitimate purposes like ad verification, data scraping, website testing, or privacy-enhancing rerouting.
Some proxy companies sell access to residential proxies and offer monetary rewards to users who agree to share their bandwidth.
In a report today, AT&T Alien Labs says that the 400,000-node proxy network was built by using malicious payloads that delivered the proxy application.
Despite the company behind the botnet claiming that users gave their consent, the researchers discovered that the proxy installed silently on the devices.
"Although the proxy website claims that its exit nodes come only from users who have been informed and agreed to the use of their device, Alien Labs has evidence that malware writers are installing the proxy silently in infected systems," AT&T Alien Labs
"In addition, as the proxy application is signed, it has no anti-virus detection, going under the radar of security companies," the researchers added.
The same company controlled exit nodes created by a malicious payload called AdLoad that targeted macOS systems, which AT&T reported last week.
In fact, the two Go-based binaries (for macOS and Windows) appear to originate from the same source code, however, the Windows proxy client evades antivirus detection due to using a valid digital signature.
Proxyware infection
The infection starts with the execution of a loader hidden in cracked software and games, which downloads and installs the proxy application automatically in the background without user interaction.
The malware authors use Inno Setup with specific parameters that hide any indicators of the installation process and all typical user prompts.
During the installation of the proxy client, the malware sends specific parameters, which are also relayed to the command and control (C2) server so that the new client can be registered and incorporated into the botnet.
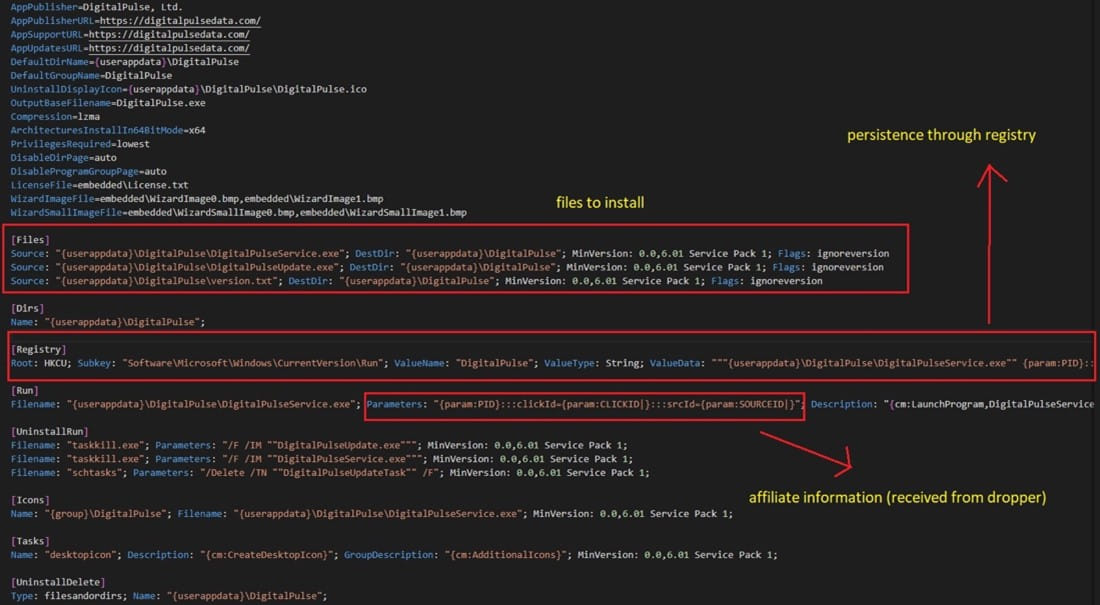
Installation and establishing persistence (AT&T)
The proxy client establishes persistence on the infected system by creating a registry key to activate it when the system boots and a by adding a scheduled task that to check for new client updates.
"The proxy then continuously gathers vital information from the machine to ensure optimal performance and responsiveness," explains the AT&T report.
"This includes everything from the process list and monitoring CPU to memory utilization and even tracking battery status."
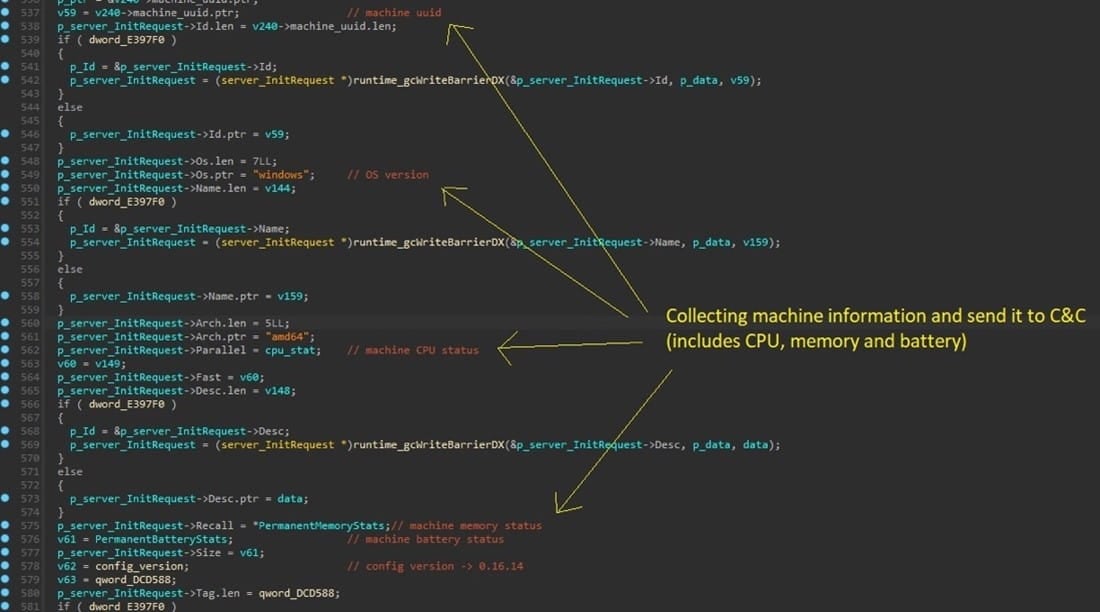
Data collection taking place on the infected device (AT&T)
How to protect
AT&T recommends looking for a "Digital Pulse" executable at "%AppData%\" or a similarly named Registry key on "HKCU\Software\Microsoft\Windows\CurrentVersion\Run\." If any are present, the researchers recommend removing them.
The name of the scheduled task is "DigitalPulseUpdateTask" and should also be deleted to eliminate the chance of the client update mechanism re-introducing the infection.
Finally, avoid downloading pirated software and running executables sourced from dubious locations like peer-to-peer networks or site offering premium software free of charge.
Signs of proxyware infection include performance and internet speed degradation, unexpected network traffic patterns, frequent communication with unknown IPs or domains, and system alerts.