The War Room
1 readers
1 users here now
Community for various OSINT news and subject matter for open discussion or dissemination elsewhere
founded 1 year ago
MODERATORS
201
202
203
204
205
206
207
1
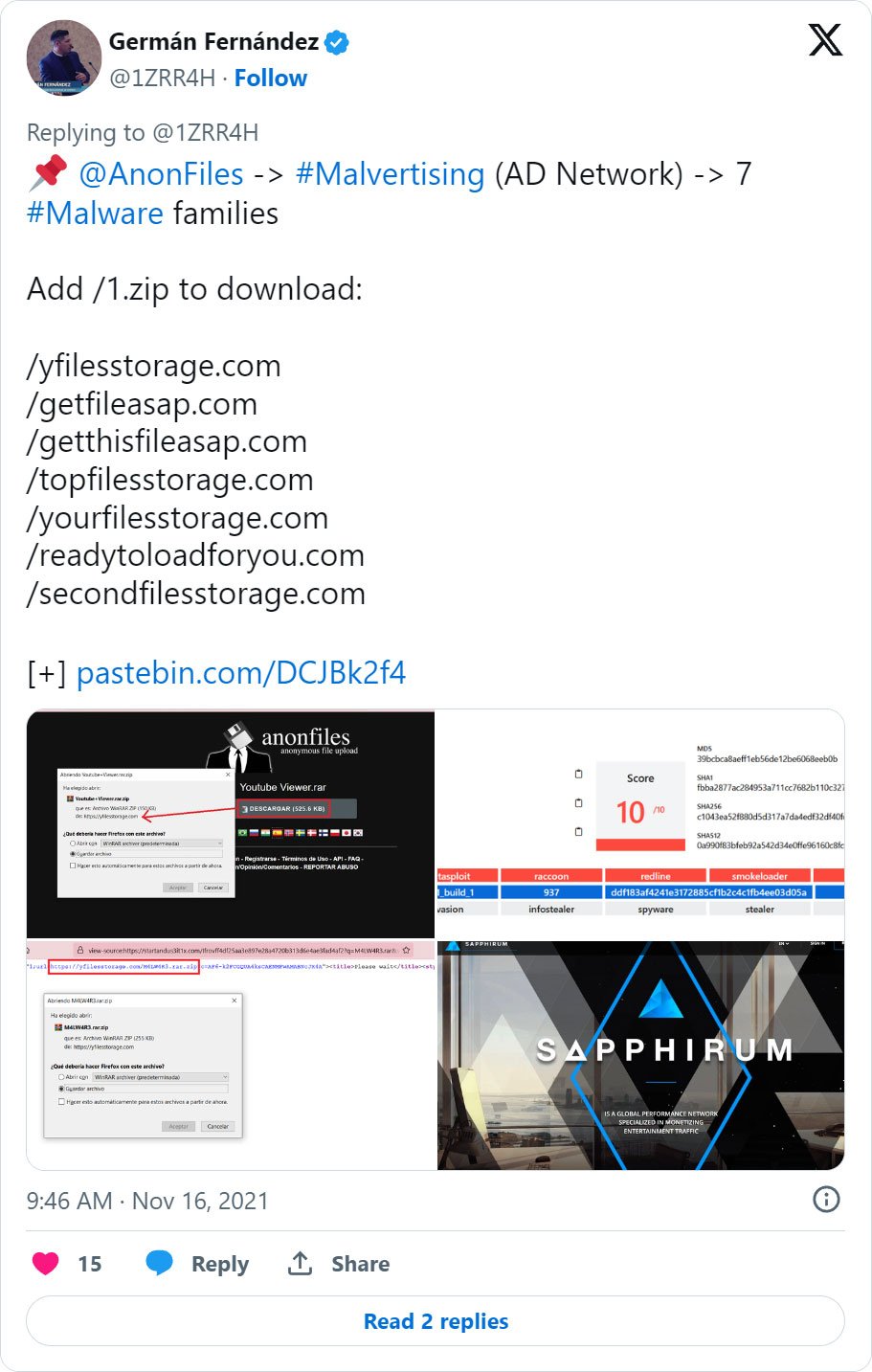
Russian Hackers Use Zulip Chat App for Covert C&C in Diplomatic Phishing Attacks
(thehackernews.com)
208
1
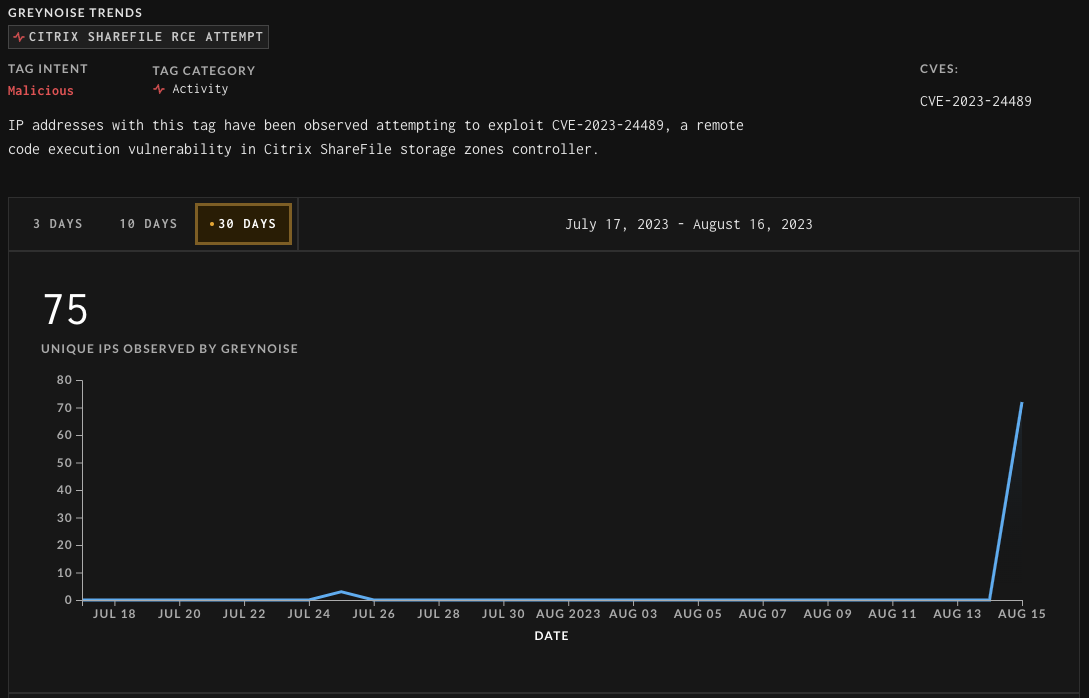
Exploitation of Citrix ShareFile Vulnerability Spikes as CISA Issues Warning
(www.securityweek.com)
209
1
Cleaning Products manufacturer Clorox Company took some systems offline after a cyberattack
(securityaffairs.com)
210
211
212
213
214
1
CISA adds flaw in Citrix ShareFile to its Known Exploited Vulnerabilities catalog
(securityaffairs.com)
215
216
217
218
1
67% of Federal Government Agencies Are Confident in Meeting Zero Trust Executive Order Deadline
(www.darkreading.com)
219
1
Call for Applications Open for DataTribe's Sixth Annual Cybersecurity Startup Challenge
(www.darkreading.com)
220
221
222
223
224
225