Microsoft has accidentally revealed an internal 'StagingTool' utility that can be used to enable hidden features, or Moments, in Windows 11.
When developing new features, Microsoft adds them to public Windows preview builds in a hidden and disabled state. These features, or Moments, can be enabled when they want to perform public A/B or internal tests.
For years, Windows enthusiasts have been searching for hidden features in new Insider preview builds and using specialized third-party tools, like ViveTool, to enable them for a sneak peek into what's coming in the future.
Now, Microsoft has revealed its own tool used to enable these hidden features.
Microsoft accidentally reveals StagingTool
As first discovered by Windows sleuth XenoPanther, Microsoft has a utility for enabling hidden development features in Windows 11 called 'StagingTool'.
While the tool was previously only used internally, Microsoft accidentally revealed its existence in a Feedback Hub quest during the August 2023 Bug Bash, an event held by Microsoft to find the most bugs in the operating system.
In this quest, Microsoft wanted users in China to test a new passwordless sign-in feature and offered instructions on using and downloading the StagingTool.exe to enable the feature.
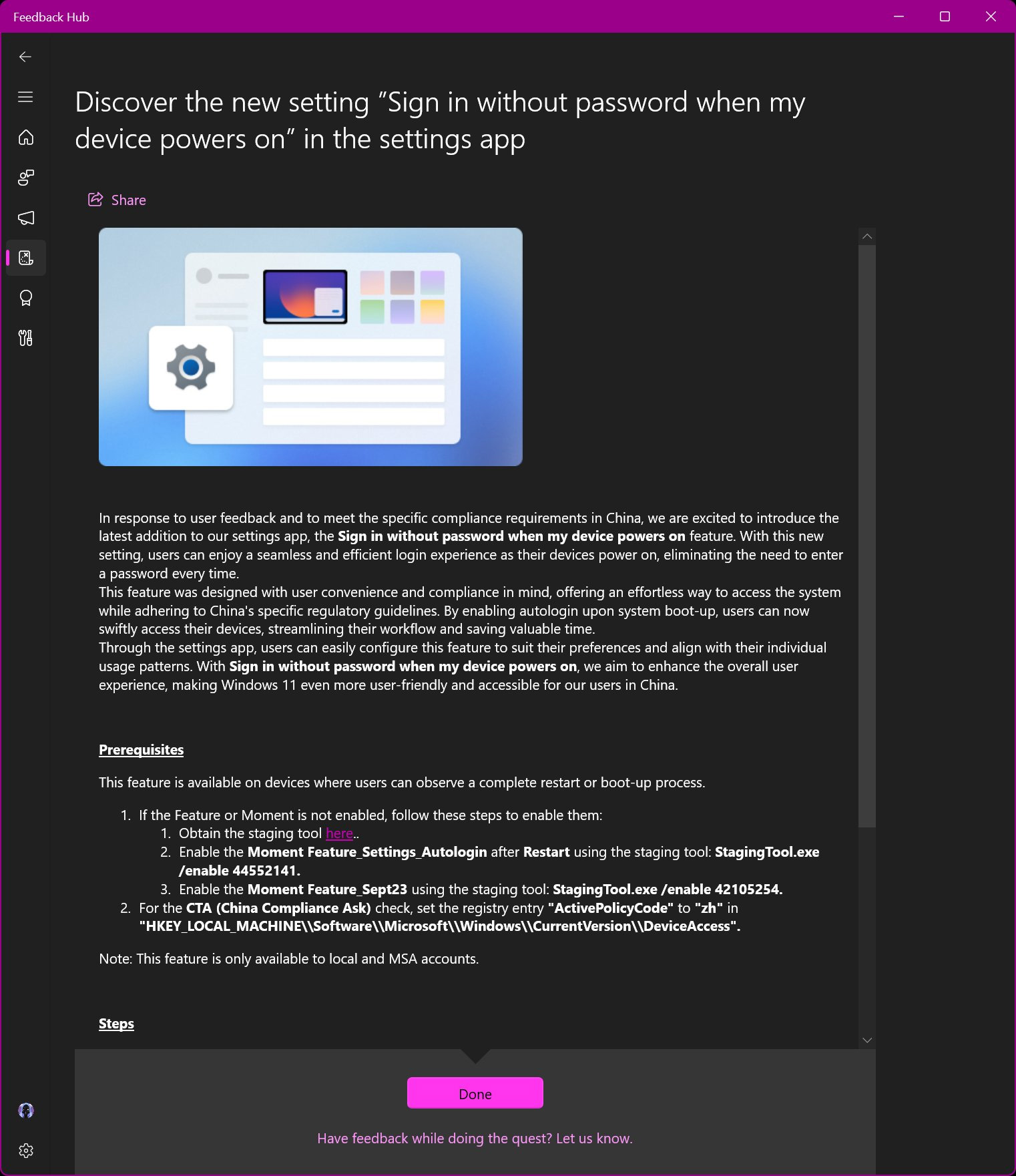
Feedback Hub question accidentally revealing linkg to StagingTool
Source: XenoPanther
While Microsoft has since made the tool unavailable, it has now been widely spread among Windows enthusiasts, allowing them to use a Microsoft-sanctioned tool to enable hidden features.
How to use the Windows StagingTool to enable hidden features
Microsoft's StagingTool is a command-line program that allows you to enable hidden features, otherwise known as Moment features, in Windows 11.
To enable a hidden feature, you must know its numeric feature ID, which Microsoft developers internally use.
However, it is possible to find new feature IDs and their associated feature name by scanning Windows 11 debug symbols (PDBs) that are released along with new preview builds. A tool called ViVeTool GUI Feature Scanner can be used to help find new feature IDs in preview builds.
Once you have a feature ID for a hidden feature you want to test, you can use Microsoft's StagingTool to enable or disable it.
To use StagingTool, you will need administrative privileges, so the tool needs to be run from an elevated command prompt in a console, such as the Command Prompt or Windows Terminal.
StagingTool includes a built-in help file that can be displayed by entering the StagingTool.exe /? command, which displays the following help text:
[StagingTool.exe] Controls the feature configurations for this device Usage: StagingTool.exe [/enable ] [/disable ] [/query [featureId]] [/reset ] [/testmode] [/setvariant [payload]] [/serialize] [/setlkg] [/restorelkg] [/trace [ ... ]] [/setbootconfigs ] /enable Enable the specified feature /disable Disable the specified feature /query Query the specified feature (or all features, if featureId is omitted) for enablement and variant information /v Optional parameter to also print ImageDefault and ImageOverride features /reset Reset the specified feature to its default state Specifies a feature by its feature Id Example: Enable features with Id 1 StagingTool.exe /enable 1 /testmode Used in conjunction with /enable /disable /reset Applied feature configs will revert after reboot /telemetry Used in conjunction with /enable /disable /reset Enables sending additional telemetry /setvariant Select a feature variant to use (note: the feature must be enabled for variants to be expressed). Use /query to list configured variants. Specifies a feature by its feature Id Specifies a feature variant by id. [payload] (Optional) Unsigned int payload for the variant (for variants that support fixed payload) /serialize Rather than apply changes to the local machine, use this option to print out (in reg.exe/hex format) a new config with all of the requested changes. This can be used for offline updates to VHDs prior to first boot. /setlkg Set Boot time feature override states as LKG Configurations /restorelkg Restore Boot time LKG configurations states Feature Configurations /trace Realtime ETW trace for the specified feature(s) usage in code E.g. enable trace for the feature with ID 1235441: StagingTool.exe /trace 1235441 /? Show command usage
Before continuing, it should be noted that these are experimental, in-development features that could cause system instability in Windows 11. Therefore, it is strongly advised that you test these features in a virtual machine to easily roll back to an earlier snapshot if something goes wrong.
With that warning shared, you can use the StagingTool.exe /query command to see a list of available feature IDs. However, this command will only list the feature ID numbers and an internal Microsoft link to information about the experiment, which is not very helpful.
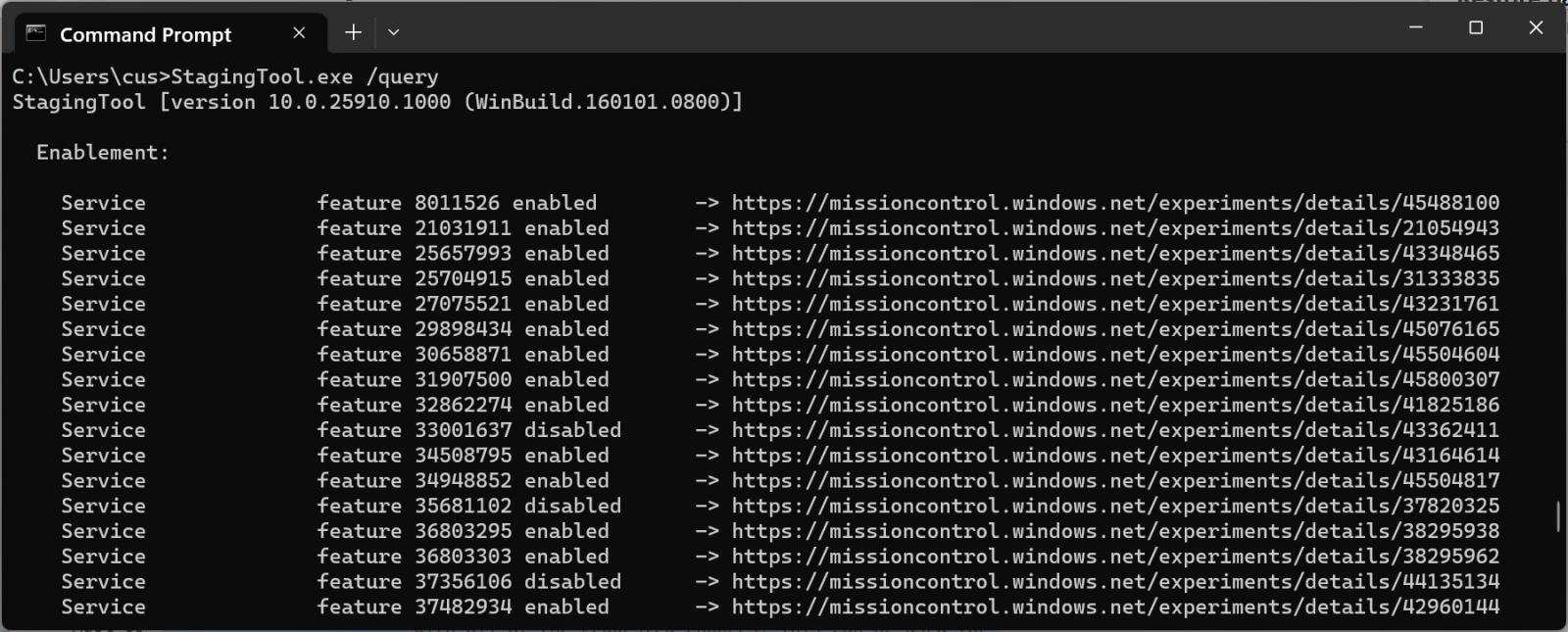
Using StagingTool to query for feature IDs
Source: BleepingComputer
If you cannot discover what a particular feature IDs is for, you can follow Windows enthusiasts on Twitter, who sometimes share new hidden features. Some recommended people to follow include Albacore, XenoPanther, Rafael Rivera, and PhantomOcean3.
To enable a hidden feature, you can use the StagingTool.exe /enable command. For example, to enable feature ID 33001637, you would use the StagingTool.exe /enable 33001637 command from an elevated command prompt.
To disable a feature, you would use the StagingTool.exe /disable command. For example, StagingTool.exe /disable 33001637.
Therefore, if you enable a hidden feature and find that it breaks something in Windows 11, you can deactivate it to resolve the conflict.
For some features, you must restart Windows 11 after enabling or disabling a new feature.
Many other StagingTool commands are for more advanced usage, likely enabling feature variants, specific payloads, or telemetry.
Two interesting commands are the /serialize and /trace command line arguments.
The trace option will debug an enabled feature using Event Tracing for Windows (ETW), while the serialize option will create a new config to enable/disable features via the Registry as offline updates to VHDs.
Serialized configuration to enable feature in VHDs
Source: BleepingComputer
However, most of these advanced features are for internal use by Microsoft and do not need to be used.
Playing with these tools to test hidden features can be fun for Windows enthusiasts, but as previously said, they can also cause instability in the operating system.
Therefore, using ViveTool or StagingTool on your main Windows 11 computer is not advised. Instead, play with them on installs you can reinstall or restore.