The War Room
1 readers
1 users here now
Community for various OSINT news and subject matter for open discussion or dissemination elsewhere
founded 1 year ago
MODERATORS
626
1
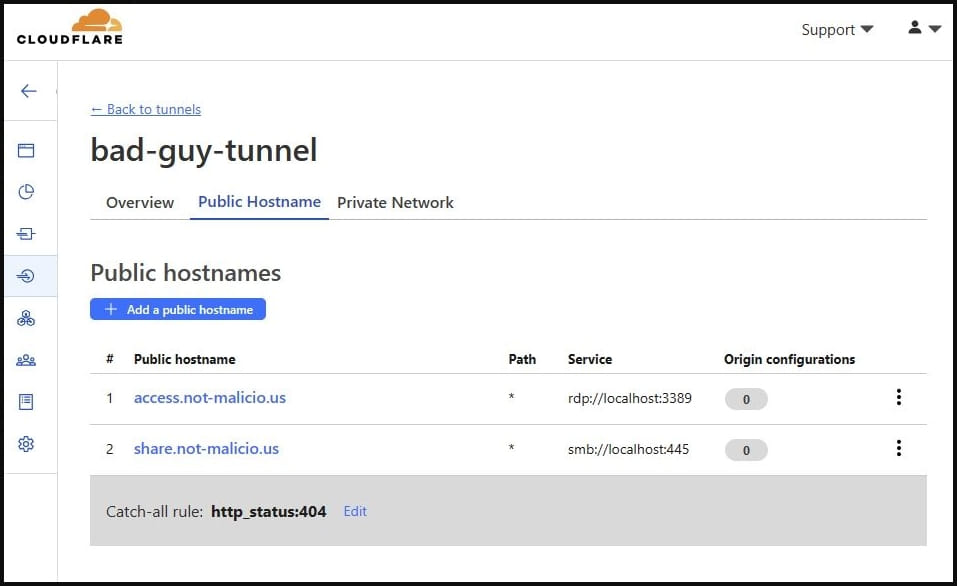
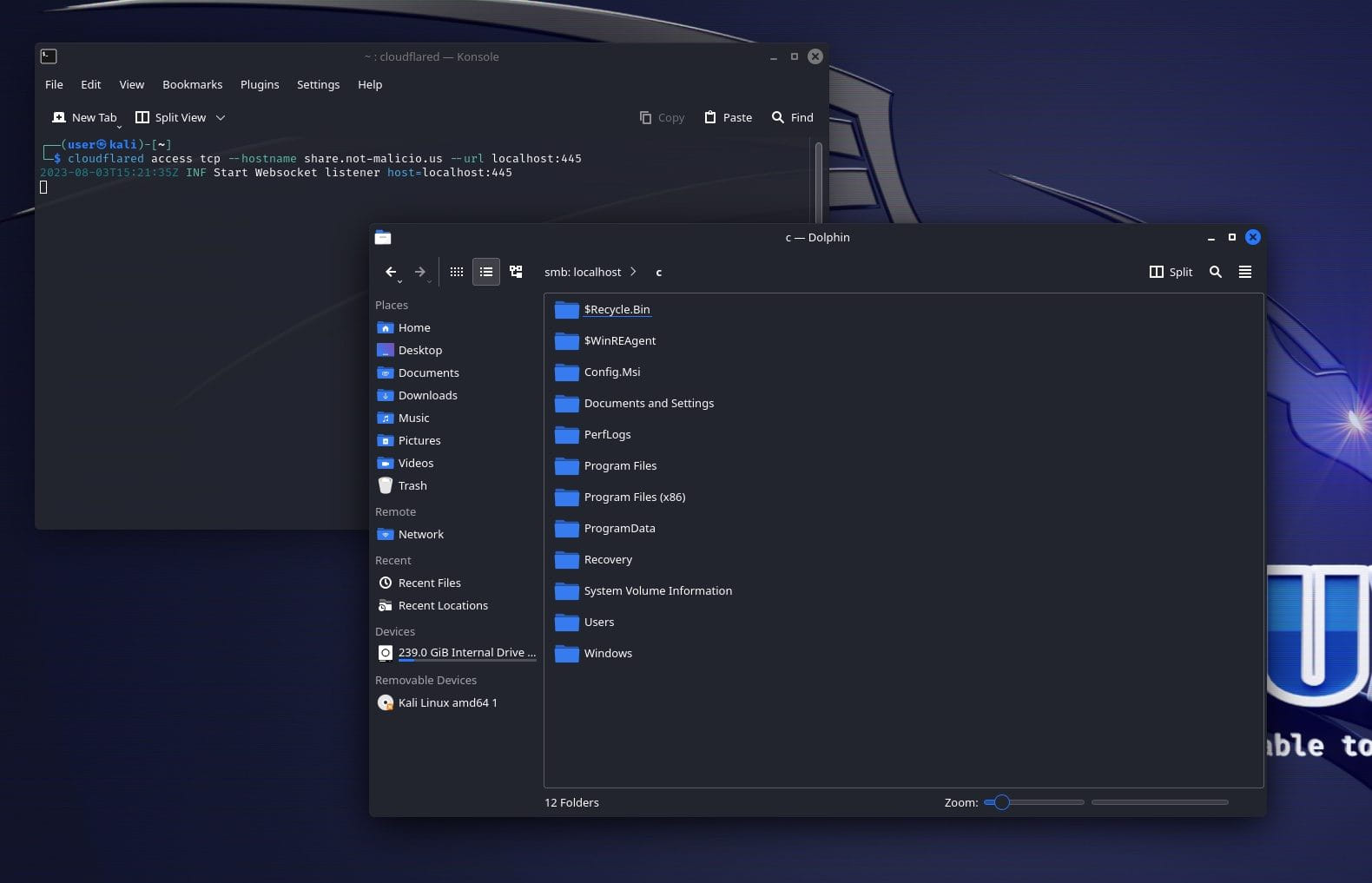
LOLBAS in the Wild: 11 Living-Off-The-Land Binaries Used for Malicious Purposes
(thehackernews.com)
627
1
Android’s August 2023 Updates Patch Critical RCE (CVE-2023-21273 & CVE-2023-21282) Bugs
(securityonline.info)
628
1
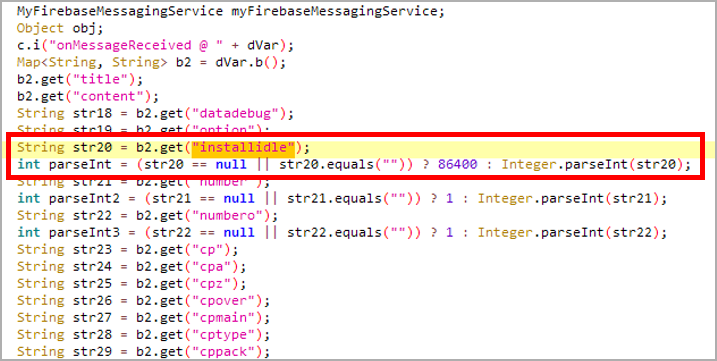
43 Android apps in Google Play with 2.5M installs loaded ads when a phone screen was off
(securityaffairs.com)
629
630
631
632
633
1
Zoom trains its AI model with some user data, without giving them an opt-out option
(securityaffairs.com)
634
635
636
637
638
639
1
Cyberinsurance Firm Resilience Raises $100 Million to Expand Its Cyber Risk Platform
(www.securityweek.com)
640
641
642
643
1
New Malware Campaign Targets Inexperienced Cyber Criminals with OpenBullet Configs
(thehackernews.com)
644
1
North Korea compromised Russian missile engineering firm NPO Mashinostroyeniya
(securityaffairs.com)
645
646
647
1
CVE-2023-3823 & CVE-2023-3824 – PHP Security Vulnerabilities: What You Need to Know
(securityonline.info)
648
649
650